The massive state-sponsored espionage campaign that compromised software maker SolarWinds also targeted Microsoft, as the unfolding investigation into the hacking spree reveals the incident may have been far more wider in scope, sophistication, and impact than previously thought.
News of Microsoft's compromise was first reported by Reuters, which also said the company's own products were then used to strike other victims by leveraging its cloud offerings, citing people familiar with the matter.
The Windows maker, however, denied the threat actor had infiltrated its production systems to stage further attacks against its customers.
In a statement to The Hacker News via email, the company said —
"Like other SolarWinds customers, we have been actively looking for indicators of this actor and can confirm that we detected malicious SolarWinds binaries in our environment, which we isolated and removed. We have not found evidence of access to production services or customer data. Our investigations, which are ongoing, have found absolutely no indications that our systems were used to attack others."
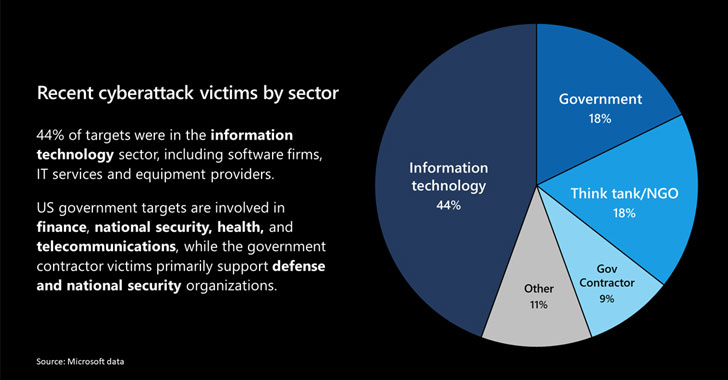
Characterizing the hack as "a moment of reckoning," Microsoft president Brad Smith said it has notified over 40 customers located in Belgium, Canada, Israel, Mexico, Spain, the UAE, the UK, and the US that were singled out by the attackers. 44% of the victims are in the information technology sector, including software firms, IT services, and equipment providers.
CISA Issues New Advisory
The development comes as the US Cybersecurity and Infrastructure Security Agency (CISA) published a fresh advisory, stating the "APT actor [behind the compromises] has demonstrated patience, operational security, and complex tradecraft in these intrusions."
"This threat poses a grave risk to the Federal Government and state, local, tribal, and territorial governments as well as critical infrastructure entities and other private sector organizations," it added.
But in a twist, the agency also said it identified additional initial infection vectors, other than the SolarWinds Orion platform, that have been leveraged by the adversary to mount the attacks, including a previously stolen key to circumvent Duo's multi-factor authentication (MFA) to access the mailbox of a user via Outlook Web App (OWA) service.
Digital forensics firm Volexity, which tracks the actor under the moniker Dark Halo, said the MFA bypass was one of the three incidents between late 2019 and 2020 aimed at a US-based think tank.
The entire intrusion campaign came to light earlier this week when FireEye disclosed it had detected a breach that also pilfered its Red Team penetration testing tools.
Since then, a number of agencies have been found to be attacked, including the US departments of Treasury, Commerce, Homeland Security, and Energy, the National Nuclear Security Administration (NNSA), and several state department networks.
While many details continue to remain unclear, the revelation about new modes of attack raises more questions about the level of access the attackers were able to gain across government and corporate systems worldwide.
Microsoft, FireEye, and GoDaddy Create a Killswitch
Over the last few days, Microsoft, FireEye, and GoDaddy seized control over one of the main GoDaddy domains — avsvmcloud[.]com — that was used by the hackers to communicate with the compromised systems, reconfiguring it to create a killswitch that would prevent the SUNBURST malware from continuing to operate on victims' networks.
For its part, SolarWinds has not yet disclosed how exactly the attacker managed to gain extensive access to its systems to be able to insert malware into the company's legitimate software updates.
Recent evidence, however, points to a compromise of its build and software release system. An estimated 18,000 Orion customers are said to have downloaded the updates containing the back door.
Symantec, which earlier uncovered more than 2,000 systems belonging to 100 customers that received the trojanized SolarWinds Orion updates, has now confirmed the deployment of a separate second-stage payload called Teardrop that's used to install the Cobalt Strike Beacon against select targets of interest.
The hacks are believed to be the work of APT29, a Russian threat group also known as Cozy Bear, which has been linked to a series of breaches of critical US infrastructure over the past year.
The latest slew of intrusions has also led CISA, the US Federal Bureau of Investigation (FBI), and the Office of the Director of National Intelligence (ODNI) to issue a joint statement, stating the agencies are gathering intelligence in order to attribute, pursue, and disrupt the responsible threat actors.
Calling for stronger steps to hold nation-states accountable for cyberattacks, Smith said the attacks represent "an act of recklessness that created a serious technological vulnerability for the United States and the world."
"In effect, this is not just an attack on specific targets, but on the trust and reliability of the world's critical infrastructure in order to advance one nation's intelligence agency," he added.
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Contact Digitpol's hotlines or respond to us online.
Digitpol is available 24/7.
Email: info@digitpol.com
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944 <br