Encryption & Key Management
,
Governance & Risk Management
,
IT Risk Management
Web Conferencing Provider Blames Routing of Keys via China on Scaling-Up Error
Zoom, responding to new research that highlighted encryption and infrastructure shortcomings in its audio and video conferencing software, has promised to further revamp its security controls.
See Also: Live Webinar | More Data, More Problems: Applying the Right Automation to Propel Security Operations
With the COVID-19 pandemic driving a surge in working from home, researchers have been closely reviewing the security of tools that support remote work and distance education and sometimes finding flaws or design decisions that need fixing.
On Friday, Citizen Lab, a group based at University of Toronto that studies surveillance and its impact on human rights, published a report warning that Zoom appeared to have a “roll your own” encryption scheme that “has significant weaknesses,” leaving communications potentially open to being intercepted. The report, written by researchers Bill Marczak and John Scott-Railton, also warned of “potential areas of concern in Zoom’s infrastructure, including [transmitting] meeting encryption keys through China.”
The Citizen Lab researchers warn that the increased use of Zoom’s teleconferencing platform means that it’s likely being used, at least in some cases, for intragovernment communications. “We suspect that this makes Zoom a high priority target for signals intelligence (SIGINT) gathering and targeted intrusion operations,” they write. Last week, British Prime Minister Boris Johnson tweeted a picture of his cabinet meeting via Zoom (see: The Cybersecurity Follies: Zoom Edition).

The researchers also reported finding a serious issue in the Zoom platform’s waiting room feature, which they’ve reported to Zoom and won’t disclose until the flaw gets fixed. “In the meantime, we advise Zoom users who desire confidentiality to not use Zoom waiting rooms,” they write. “Instead, we encourage users to use Zoom’s password feature, which appears to offer a higher level of confidentiality than waiting rooms.”
Zoom CEO Eric Yuan responded rapidly to the Citizen Lab report, saying that Zoom would implement geo-fencing and meeting encryption to address the findings, as well as promising further changes. “We appreciate the questions we are getting, and continue to work actively to address issues as we identify them,” Yuan says in a Friday blog post. “As video communications become more mainstream, users deserve to better understand how all these services work, including how the industry – Zoom and its peers – manages operations and provides services in China and around the world.”
Citizen Lab did not review Zoom for Government, which is a paid service that offers additional security controls.
Conferencing App Adoption Surges
Use of conferencing applications has surged in recent weeks as the COVID-19 pandemic has led to governments ordering people to stay at home. The near-overnight shift to working from home for numerous employees, as well as students, has led to a massive uptake in applications such as Zoom, WebEx, Skype, Microsoft Teams and other tools.
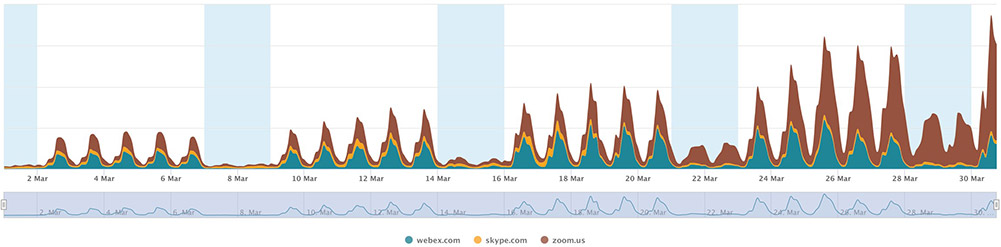
“We continue to see – especially in the U.S. – the dramatic growth in conferencing applications, especially Zoom, which has experienced over 700 percent of growth from Feb. 1,” says Craig Labovitz, a CTO at Nokia, in a blog post.
But security questions over Zoom have led to some organizations blocking its use (see: Zoom Rushes Patches for Zero-Day Vulnerabilities).
New York City’s Department of Education, for example, has banned teachers from using Zoom for remote teaching of 1.1 million students across 1,800 city schools, and is instead adopting Microsoft Teams. A spokesman tells TechCrunch that the software has the “same capabilities with appropriate security measures in place.”
Zoom: Security Problems
Findings from the Citizen Lab report on the free version of Zoom’s software have created further cause for concern.
Citizen Lab reports that while Zoom claims to use AES-256 encryption, it only saw AES-128 keys being used. “Using smaller than recommended AES keys is not ideal. It’s not disastrous but it does make one question why they would do it,” Alan Woodward, a professor of computer science at the University of Surrey, tells Information Security Media Group.
Also of concern: Zoom uses AES-128 in electronic code book – ECB – mode, to encrypt and decrypt audio and video, according to the report.
“The use of ECB on an image-based system is really strange,” Woodward says. “Even a first-year student knows that in such systems identical blocks of plaintext will result in identical cipher text which is a gift to any cryptanalyst,” Woodward says, because it makes it easy to decipher what has been encrypted.
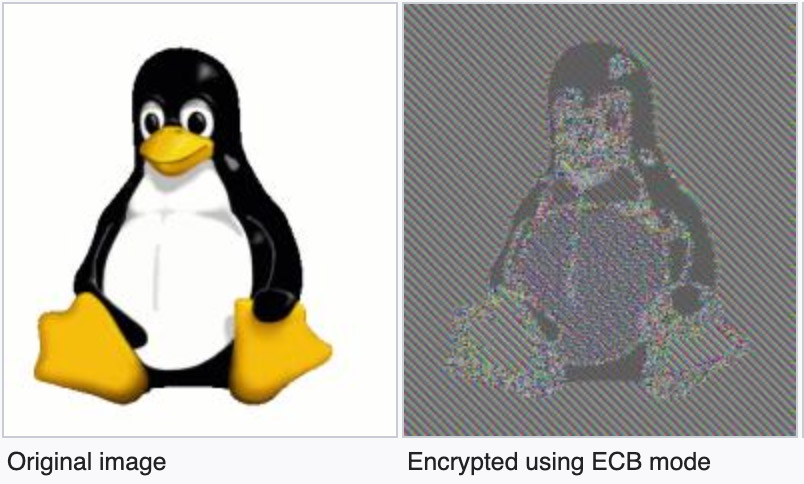
“When companies roll their own crypto, I expect it to have flaws. I don’t expect those flaws to be errors I’d find unacceptable in an introductory undergraduate class, but that’s what happened here,” says Steven M. Bellovin, a professor in the computer science department at Columbia University.
In terms of ECB, “it’s probably not a real threat – I doubt if anyone but a major SIGINT agency could exploit it – but it’s just one of these things that you should absolutely never do,” he says. “It suggests that the encryption code was written by someone who knew nothing whatsoever about the subject – and lays open the suspicion that there are deeper, more subtle problems. I mean, subtle problems are hard to avoid in cryptography even when you know what you’re doing.”
In addition, it means that whatever the software might promise, there can be no true “end-to-end encryption,” because message content can potentially be deciphered.
For sending voice and video, Zoom also appears to have created its own transmission protocol, based on a customized version of real-time transport protocol – RTP – “rather than using a standard protocol,” Citizen Lab reports.
“As with their homegrown crypto scheme, that way lies risk, especially when it’s not transparent or subject to full security audit,” Woodward says.
Key Questions
Another security shortfall cited by Citizen Lab is that keys get generated by Zoom’s servers, but were sometimes delivered by servers based in China, “even when all meeting participants, and the Zoom subscriber’s company, are outside of China.”
“The fact that the keys appear to be capable of being stored by Zoom servers, and that some of those are run by Chinese companies, does raise the obvious concerns as the Chinese have coercive laws such as Intelligence Act 2017,” Woodward says. That law could be used by the Chinese government to order a company to act in a manner that might harm other nations (see: Will UK’s Huawei Decision Become a 5G Rollout Blueprint?). While Zoom is headquartered in Silicon Valley, at least 700 of its employees reportedly work from China, including on engineering and research-and-development teams.
Zoom Provides Fixes, Promises
In response to Citizen Lab’s report, Zoom immediately promised to implement geo-fencing to ensure that no keys get routed via China, except for China-based users.
Yuan attributed the routing of keys via China to a development error as the company attempted to rapidly scale up to meet a surge of demand, starting in China, where the COVID-19 outbreak began, leading the company to allow much greater, free access to its tool, in part, to support medical professionals. (Free versions typically otherwise have a 40-minute time limit for meetings.)
“In February, Zoom rapidly added capacity to our Chinese region to handle a massive increase in demand,” Yuan says. “In our haste, we mistakenly added our two Chinese data centers to a lengthy whitelist of backup bridges, potentially enabling non-Chinese clients to – under extremely limited circumstances – connect to them (namely when the primary non-Chinese servers were unavailable). This configuration change was made in February.”
He says Zoom fixed this problem immediately after learning of it via Citizen Lab.
“We have also been working on improving our encryption and will be working with experts to ensure we are following best practices,” Yuan says.
But Bellovin says the company will have its work cut out for it. “Zoom is doing its cryptography very badly, and while some of the errors can be fixed pretty easily, others are difficult and will take time and expertise to solve,” he says.
Appropriate Uses
Citizen Lab says its findings demonstrate that the free version of Zoom is “not suited for secrets.” But that doesn’t mean the software should be avoided altogether. “We’re not claiming that this is evidence that you should forever delete the app,” Citizen Lab’s Marczak tells the Wall Street Journal. “If you’re having a virtual hangout with our friends, you’re probably fine. If you’re discussing classified information, you should maybe think twice.”
“Zoom is not suitable for conversations involving ‘top secret’ clearance topics, highly sensitive intellectual property concerns, dangerous whistleblowing against a repressive government, or planning and executing criminal conspiracies. If these are your remote work activities, Zoom is not right for you,” says Tod Beardsley, director of research at security firm Rapid7 and an avowed Zoom user. “If you are comfortable with normal telephone calls, public meetings, or casual video calls on pretty much any other platform, Zoom is almost certainly ‘good enough.'”
Stay-at-Home Considerations
University of Surrey’s Woodward also finds such tools still suitable for many non-sensitive use cases.
“If I wanted to have a conversation that was sensitive, I probably wouldn’t use videoconferencing anyway unless I had a secure facility – i.e. not home-to-home,” Woodward says. “However, for most purposes in the current situation it is often better to enable mass communication to get people to observe the stay-at-home rules.”
At the same time, whatever a vendor might claim in terms of encryption or security, only believe in what’s been audited and proven.
“But don’t assume anything other than those apps which have been security audited are really secure,” Woodward says. “For a company, do your due diligence. e.g. look for where security audits have been done such as with WhatsApp and Signal. And if in any doubt, seek advice from those who truly understand cybersecurity.”
(See also: Prosecutors: ‘Zoom-Bombing’ Could Lead to Charges
)
[ad_2]
Article Source link
Is your business effected by a COVID-19 / Coronavirus related Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Contact Digitpol’s hotlines or respond to us online.
Digitpol is available 24/7.
Email: info@digitpol.com
Europe +31558448040
UK +44 20 8089 9944
ASIA +85239733884
