Researchers have outlined the most popular tools and techniques used by threat actors to try and bypass Microsoft’s Antimalware Scan Interface (AMSI).
Making its debut in 2015, AMSI is a vendor-agnostic interface designed to integrate anti-malware products on a Windows machine and better protect end users, supporting features including scan request correlation and content source URL/IP reputation checks.
AMSI’s integration with Office 365 was recently upgraded to include Excel 4.0 (XLM) macro scanning to try and combat the increase of malicious macros as an infection vector.
Microsoft’s security solution is a barrier that today’s Windows malware developers often try to circumvent — either by methods such as obfuscation, steganography, or by preventing a file from being scanned and detected as malicious in initial attack stages.
In an investigation into techniques used to either avoid or disable AMSI, Sophos researchers said on Wednesday that threat actors will try everything from living-off-the-land tactics to fileless attacks.
Perhaps the opportunities AMSI bypass represents were highlighted in a tweet by security expert Matt Graeber in 2016, in which Sophos says a single line of code flipped a PowerShell attribute for AMSI integration and, in theory, may have stopped PowerShell-based processes from requesting scans.
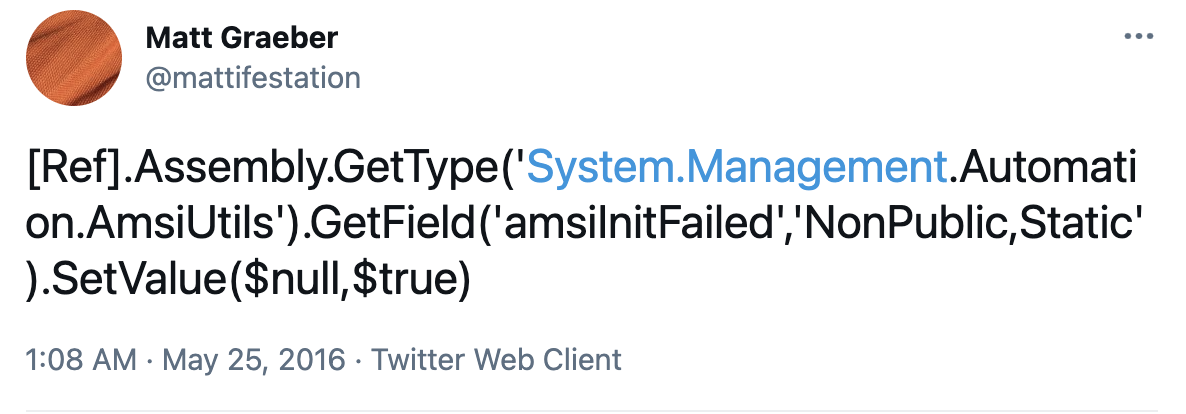
While now integrated and flagged as malicious now for years, malware developers have taken inspiration from the one-line AMSI bypass and variations are still in use today that have been obfuscated to try and dance around signature-based scans.
In detections over 2020 – 2021, the majority appear to be focused on post-exploitation activities, including lateral movement. One method, for example, attempts to retrieve a PowerShell backdoor from a web server within a private IP address space.
The same bypass was traced back to a separate incident, linked to Proxy Logon attacks, in which a connection was forged to a remote server in order to grab a PowerShell-based malware downloader.
Another technique used for AMSI bypass is the use of Seatbelt, an offensive security tool. A PowerShell script was used to create a delegate process that uses reflection to access the .NET interface for AmsiUtils.
However, Sophos says that over 98% of AMSI circumvention attempts are made through tampering with the AMSI library. There are a variety of malware strains that will try to find AmsiScanBuffer, already loaded into memory, and then overwrite instructions to make sure scan requests fail.
Alternative versions may modify the memory component storing the code designed to return buffer scan results, prompting failure.
Other tactics include:
- Cobalt Strike: The memory patch technique is included under amsi_disable, and is viewable in the Agent Tesla Trojan family, alongside others.
- Command line remote scripts invoked in PowerShell prior to patch attempts.
- Creating fake DLLs designed to dupe PowerShell into loading a fake version of amsi.DLL, an old tactic now made more difficult due to improved Microsoft security.
- Downgrading script engines.
- Loading unsupported engines, or in extreme cases, virtual machines (VMs).
“Given how prevalent those tactics have become, particularly in ransomware operator intrusions, AMSI can play a particularly important role in keeping Windows 10 and Windows Server systems from being compromised,” Sophos says. “But AMSI is not a panacea. And while Microsoft’s Windows Defender provides some protection against AMSI bypasses, attackers are continuously finding ways to obfuscate and conceal malicious content from anti-malware signature detections.”
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Digitpol can assist with all stages of cyber related incidents.
Contact Digitpol’s hotlines or respond to us online.
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944
