Cybersecurity researchers today disclosed a new supply-chain attack targeting the Vietnam Government Certification Authority (VGCA) that compromised the agency’s digital signature toolkit to install a backdoor on victim systems.
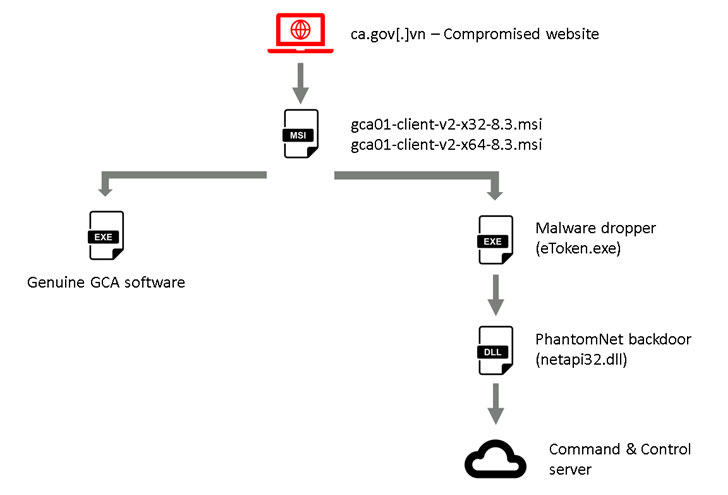
Uncovered by Slovak internet security company ESET early this month, the “SignSight” attack involved modifying software installers hosted on the CA’s website (“ca.gov.vn”) to insert a spyware tool called PhantomNet or Smanager.
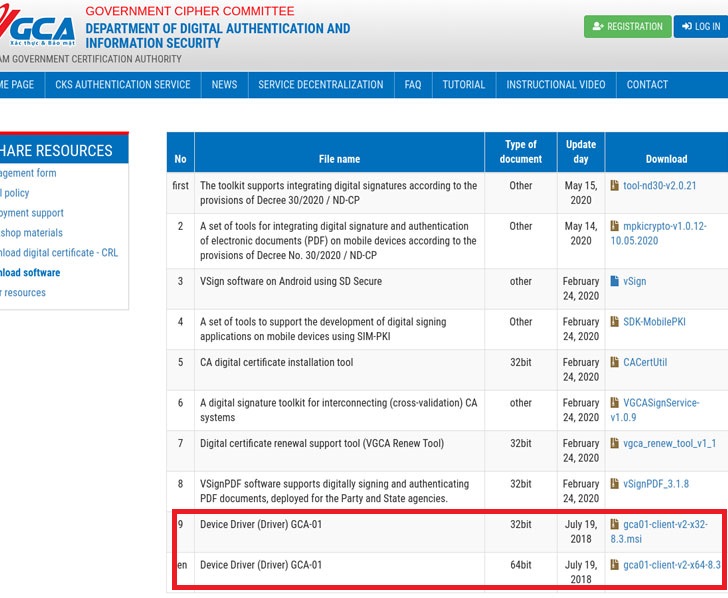
According to ESET’s telemetry, the breach happened from at least July 23 to August 16, 2020, with the two installers in question — “gca01-client-v2-x32-8.3.msi” and “gca01-client-v2-x64-8.3.msi” for 32-bit and 64-bit Windows systems — tampered to include the backdoor.
“The compromise of a certification authority website is a good opportunity for APT groups, since visitors are likely to have a high level of trust in a state organization responsible for digital signatures,” ESET’s Matthieu Faou said.
After the attack was reported to VGCA, the certificate authority confirmed that “they were aware of the attack before our notification and that they notified the users who downloaded the trojanized software.”
The digital signature tool, mandated by Vietnam’s Government Cipher Committee as part of an electronic authentication scheme, is used by the government sector as well as private companies to digitally sign documents using a USB token (also called a PKI token) that stores the digital signature and requires the aforementioned driver to operate.
As a consequence, the only way a user can get infected is when the compromised software hosted on the official website is manually downloaded and executed on the target system.
Once installed, the modified software starts the genuine GCA program to mask the breach and then runs the PhantomNet backdoor that masquerades as a seemingly harmless file named “eToken.exe.”
The backdoor — compiled most recently on April 26 — takes the responsibility of collecting system information, with additional malicious capabilities deployed through plugins retrieved from hardcoded command-and-control servers (e.g. “vgca.homeunix[.]org” and “office365.blogdns[.]com”) that mimic the names of VGCA and popular productivity software.
ESET said in addition to Vietnam, it saw victims in the Philippines, but their delivery mechanism remains unknown. The ultimate goal of the attackers remains unclear as well, what with little to no information about the post-compromise activity.
If anything, the incident highlights why supply-chain attacks are increasingly becoming a common attack vector among cyberespionage groups, as it allows the adversaries to deploy malware on many computers at the same time covertly.
In November, ESET disclosed a Lazarus campaign in South Korea that used legitimate security software and stolen digital certificates to distribute remote administration tools (RATs) on target systems.
Then last week, it also found that a chat software called Able Desktop, used by 430 government agencies in Mongolia, was abused to deliver the HyperBro backdoor, the Korplug RAT, and another Trojan called Tmanger.
Lastly, a supply-chain attack on SolarWinds Orion software discovered this week was exploited to breach several major US government agencies, including the Departments of Homeland Security, Commerce, Treasury, and State.
“Supply-chain attacks are typically hard to find, as the malicious code is generally hidden among a lot of legitimate code, making its discovery significantly more difficult,” Faou concluded.
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Contact Digitpol’s hotlines or respond to us online.
Digitpol is available 24/7.
Email: info@digitpol.com
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944