Cybersecurity researchers on Monday took the wraps off a new Android trojan that takes advantage of accessibility features on the devices to siphon credentials from banking and cryptocurrency services in Italy, the U.K., and the U.S.
Dubbed “SharkBot” by Cleafy, the malware is designed to strike a total of 27 targets — counting 22 unnamed international banks in Italy and the U.K. as well as five cryptocurrency apps in the U.S. — at least since late October 2021 and is believed to be in its early stages of development, with no overlaps found to that of any known families.
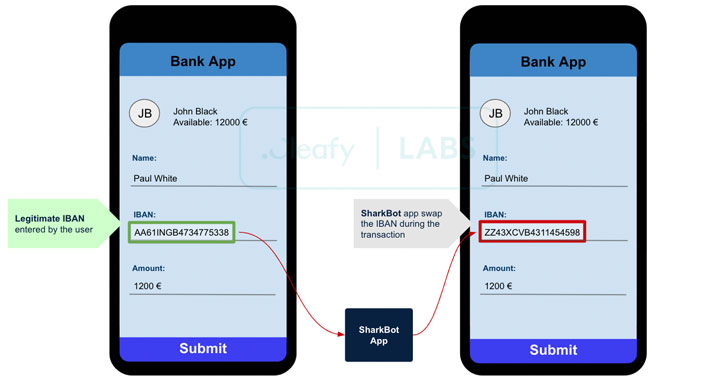
“The main goal of SharkBot is to initiate money transfers from the compromised devices via Automatic Transfer Systems (ATS) technique bypassing multi-factor authentication mechanisms (e.g., SCA),” the researchers said in a report.
“Once SharkBot is successfully installed in the victim’s device, attackers can obtain sensitive banking information through the abuse of Accessibility Services, such as credentials, personal information, current balance, etc., but also to perform gestures on the infected device.”
Masquerading as a media player, live TV, or data recovery apps, SharkBot, like its other malware counterparts TeaBot and UBEL, repeatedly prompts users with rogue pop-ups to grant it wide permissions only to steal sensitive information. Where it stands apart is the exploitation of accessibility settings to carry out ATS attacks, which allow the operators to “auto-fill fields in legitimate mobile banking apps and initiate money transfers from the compromised devices to a money mule network controlled by the [threat actor].”
The modus operandi effectively obviates the need for enrolling a new device to perform fraudulent activities, while also bypassing two-factor authentication mechanisms put in place by the banking applications.
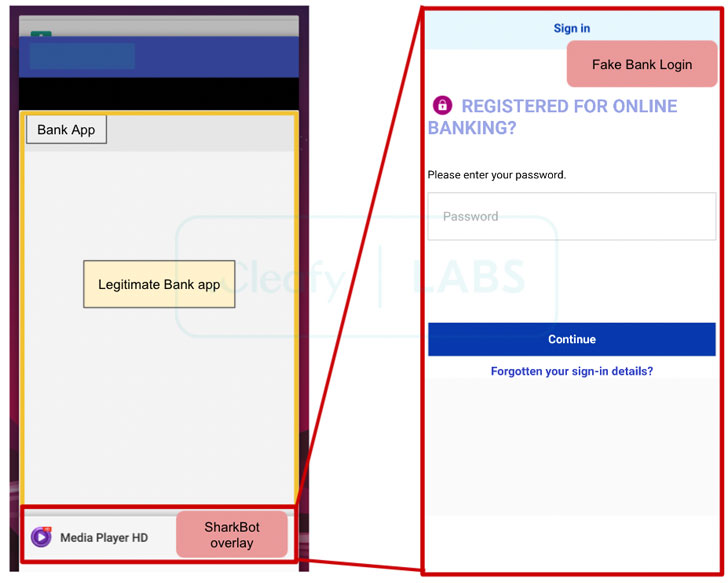
In addition, the malware comes with all features now observed across all Android banking trojans, such as the ability to perform overlay attacks to steal login credentials and credit card information, intercept legitimate banking communications sent through SMS, enable keylogging, and obtain full remote control of the compromised devices.
SharkBot is also notable for the steps it takes to evade analysis and detection, including running emulator checks, encrypting command-and-control communications with a remote server, and hiding the app’s icon from the home screen post-installation. No samples of the malware have been detected on the official Google Play Store, implying that the malicious apps are installed on the users’ devices either via sideloading or social engineering schemes.
The discovery of SharkBot in the wild shows “how mobile malwares are quickly finding new ways to perform fraud, trying to bypass behavioural detection countermeasures put in place by multiple banks and financial services during the last years,” the researchers said.
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Digitpol can assist with all stages of cyber related incidents.
Contact Digitpol’s hotlines or respond to us online.
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944