A number of high-profile Android apps are still using an unpatched version of Google’s widely-used app update library, potentially putting the personal data of hundreds of millions of smartphone users at risk of hacking.
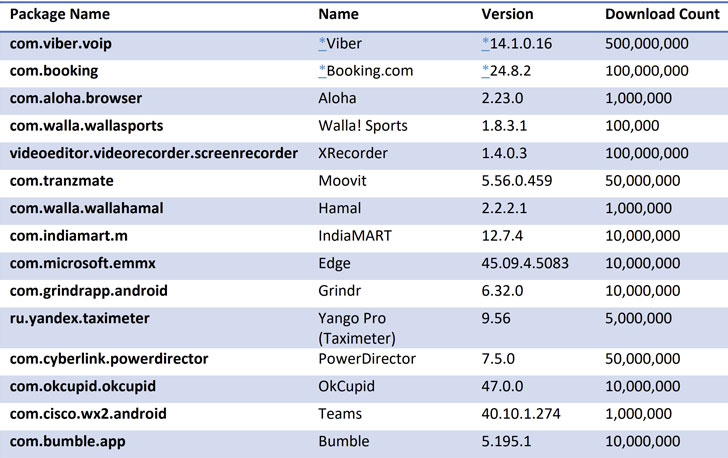
Many popular apps, including Grindr, Bumble, OkCupid, Cisco Teams, Moovit, Yango Pro, Microsoft Edge, Xrecorder, and PowerDirector, are still vulnerable and can be hijacked to steal sensitive data, such as passwords, financial details, and e-mails.
The bug, tracked as CVE-2020-8913, is rated 8.8 out of 10.0 for severity and impacts Android’s Play Core Library versions prior to 1.7.2.
Although Google addressed the vulnerability in March, new findings from Check Point Research show that many third-party app developers are yet to integrate the new Play Core library into their apps to mitigate the threat fully.
“Unlike server-side vulnerabilities, where the vulnerability is patched completely once the patch is applied to the server, for client-side vulnerabilities, each developer needs to grab the latest version of the library and insert it into the application,” the cybersecurity firm said in a report.
Play Core Library is a popular Android library that allows developers to manage the delivery of new feature modules effectively, trigger in-app updates at runtime, and download additional language packs.
First reported in late August by researchers at app security startup Oversecured, the issue allows a threat actor to inject malicious executables to any app relying on the library, thus granting the attacker full access to all the resources as that of the compromised application.
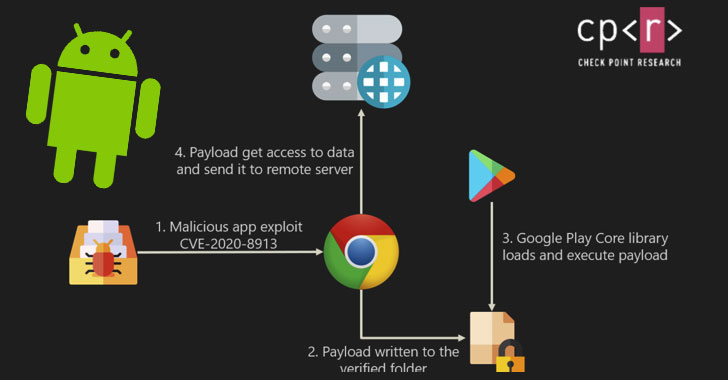
The flaw stems from a path traversal vulnerability in the library that could be exploited to load and execute malicious code (e.g., an APK file) onto a target app to steal users’ login details, passwords, financial details, and other sensitive information stored in it.
The consequences of successful exploitation of this flaw are enormous. It can be used to “inject code into banking applications to grab credentials, and at the same time have SMS permissions to steal the two-factor authentication (2FA) codes,” grab messages from chat apps, spy on users’ locations, and even gain access to corporate resources by tampering with enterprise apps.
According to Check Point Research, of the 13% of Google Play applications analyzed in the month of September 2020, 8% of those apps had a vulnerable version.
After the cybersecurity firm responsibly disclosed their findings, Viber, Meetup, and Booking.com updated their apps to the patched version of the library.
The researchers also demonstrated a proof-of-concept that used a vulnerable version of the Google Chrome app to siphon the bookmarks stored in the browser through a dedicated payload.
“We’re estimating that hundreds of millions of Android users are at security risk,” Check Point’s Manager of Mobile Research, Aviran Hazum, said. “Although Google implemented a patch, many apps are still using outdated Play Core libraries. The vulnerability CVE-2020-8913 is highly dangerous, [and] the attack possibilities here are only limited by a threat actor’s imagination.”
Update — Following the publication of the story, Cisco, Grindr, and Moovit have updated their respective apps to address the issue.
“Cisco addressed this vulnerability in the latest version of Cisco Webex Teams, released in the Google Play Store on Dec 2, 2020,” the company said in a statement to The Hacker News.
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Contact Digitpol’s hotlines or respond to us online.
Digitpol is available 24/7.
Email: info@digitpol.com
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944