Endpoint Security
,
Multi-factor & Risk-based Authentication
,
Security Operations
Check Point: Hackers Targeted Iranian Dissidents With Various Methods
A recently uncovered hacking group that has targeted Iranian dissidents for several years has developed malware that can bypass two-factor authentication protection on Android devices to steal passwords, according to a paper published by Check Point Research on Friday.
See Also: 451 Research Report: Tackling the Visibility Gap in Information Security
Besides Android devices, the hacking group which Check Point researchers call “Rampant Kitten,” has developed other malicious tools used to steal information and personal data from Windows devices and Telegram accounts, according to the report.
This hacking group, active for at least six years, has mainly targeted Iranian dissidents and expatriates, according to the report. Check Point did not indicate whether Rampant Kitten works on behalf of the Iranian government or is conducting these espionage campaigns on its own.
“According to the evidence we gathered, the threat actors, who appear to be operating from Iran, take advantage of multiple attack vectors to spy on their victims, attacking victims’ personal computers and mobile devices,” the Check Point report notes.
Hacking attempts by various groups tied to Iran’s government have dominated the news this past week as the U.S. Justice Department and federal prosecutors unsealed a series of indictments concerning Iranian attacks aimed at government agencies and private businesses both in America as well as other parts of the world (see: 3 Iranian Hackers Charged With Targeting US Satellite Firms).
The Treasury Department also announced economic sanctions this week aimed at an Iranian advanced persistent threat group, 45 associated individuals and a front company the Iranian government allegedly used to run a years-long malware campaign that targeted Iranian dissidents (see: US Imposes Sanctions on Iranian APT Group).
The U.S. Cybersecurity and Infrastructure Security Agency also warned of increased hacking activity by an Iranian-connected hacking group called “Pioneer Kitten” that has been taking advantage of vulnerabilities in VPN and other networking products (see: Iranian Hackers Exploiting Unpatched Vulnerabilities).
Bypassing 2FA
As part of its research into the six-year Rampant Kitten campaign, Check Point found that the hacking group has created malware that allows them to bypass two-factor authentication protections used in Android devices to steal SMS messages that have one-time passwords as well as other data.
In this case, the malware is disguised as a legitimate Android app. If installed, however, it functions as a backdoor that can give access to the device, according to the report. The one example that Check Point found was an app designed to help Iranian citizens get a Swedish driver’s license, although the researchers note there could be other malicious apps as well.
If the app is installed on an Android device, it will first collect information such as a list of contacts and previous SMS messages, according to the report. It can also capture voice recordings by turning on the microphone and will also call out and connect to a command-and-control server.
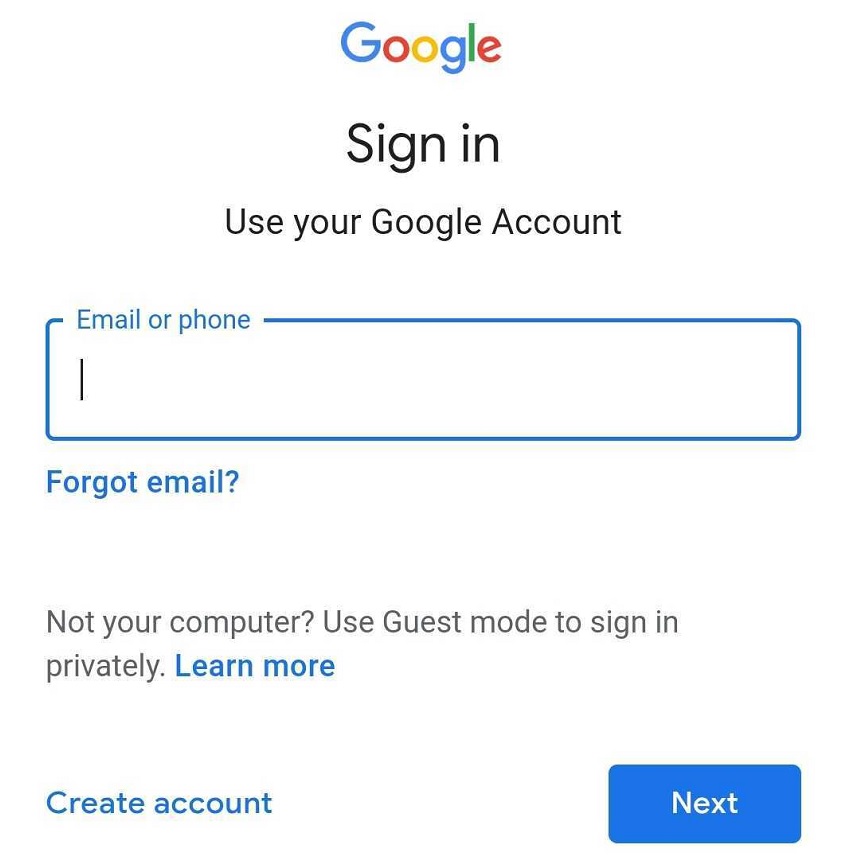
The malware appears designed to look for SMS messages that contain a “G-” string, which is a prefix used by Google as part of the two-factor authentication process. If the targeted victim was using this protection, then the hackers could capture any one-time passwords sent to the user as part of that process, according to the report.
In this case, Check Point researchers found that the hackers would send phishing emails designed as legitimate Google messages to potential victims with instructions to log into their account. These malicious messages would then capture the victim’s credentials and, if the two-factor authentication process was in place, the threat actors could bypass those security protocols as well.
The report notes that while this malware is actively being used, it appears that hackers continue to refine their malicious code.
“During our analysis, it was often obvious that this malicious application was still being actively developed, with various assets and functions which were either leftovers of previous operations, or not yet utilized,” according to the report.
By forwarding all SMS messages to the hacking group, Check Point notes that the threat actors could also capture one-time passwords for Telegram and other social media apps.
While two-factor authentication can protect devices and users, security researchers have warned that hacking groups and even cybercriminals are getting better at bypassing these security features. Earlier this week, Kaspersky researchers found that a new version of the Cerberus mobile banking Trojan can now steal two-factor authentication passcodes – even those using Google Authenticator (see: Attacks Using Cerberus Banking Trojan Surge ).
Other Attacks
In addition to the malware used to bypass two-factor authentication, the Check Point researchers note that Rampant Kitten deploys at least four separate Windows information stealers that can capture a wide range of personal data, including victims’ Telegram desktop and KeePass – an open source password manager – account information.
The Check Point researchers also found that the hacking group used phishing pages designed to appear like legitimate Telegram messages, which are designed to steal credentials and deliver other malware that can allow attackers to maintain persistence on compromised devices, according to the report.
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Contact Digitpol’s hotlines or respond to us online.
Digitpol is available 24/7.
Email: info@digitpol.com
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944
