Cloudflare said it’s system managed to stop the largest reported DDoS attack in July, explaining in a blog post that the attack was 17.2 million requests-per-second, three times larger than any previous one they recorded.
Cloudflare’s Omer Yoachimik explained in a blog post that the company serves over 25 million HTTP requests per second on average in 2021 Q2, illustrating the enormity of the attack.
He added that the attack was launched by a botnet that was targeting a financial industry customer of Cloudflare. It managed to hit the Cloudflare edge with over 330 million attack requests within seconds, he said.
Cloudflare
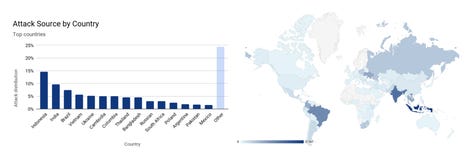
“The attack traffic originated from more than 20,000 bots in 125 countries around the world. Based on the bots’ source IP addresses, almost 15% of the attack originated from Indonesia and another 17% from India and Brazil combined. Indicating that there may be many malware infected devices in those countries,” Yoachimik said.
“This 17.2 million rps attack is the largest HTTP DDoS attack that Cloudflare has ever seen to date and almost three times the size of any other reported HTTP DDoS attack. This specific botnet, however, has been seen at least twice over the past few weeks. Just last week it also targeted a different Cloudflare customer, a hosting provider, with an HTTP DDoS attack that peaked just below 8 million rps.”
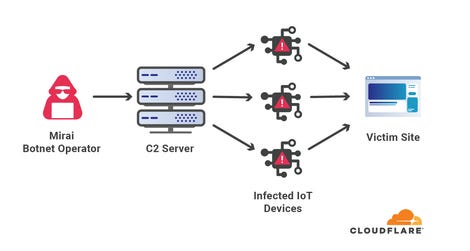
Yoachimik noted that two weeks before that, a Mirai-variant botnet “launched over a dozen UDP and TCP based DDoS attacks that peaked multiple times above 1 Tbps, with a max peak of approximately 1.2 Tbps.”
Cloudflare customers — including a gaming company and a major APAC-based telecommunications and hosting provider — are being targeted with attacks on both the Magic Transit and Spectrum services as well as the WAF/CDN service.
According to Yoachimik, the Mirai botnet generated a significant volume of attack traffic despite shrinking to about 28,000 after starting with about 30,000 bots.
“These attacks join the increase in Mirari-based DDoS attacks that we’ve observed on our network over the past weeks. In July alone, L3/4 Mirai attacks increased by 88% and L7 attacks by 9%,” Yoachimik said.
“Additionally, based on the current August per-day average of the Mirai attacks, we can expect L7 Mirai DDoS attacks and other similar botnet attacks to increase by 185% and L3/4 attacks by 71% by the end of the month.”
Tyler Shields, CMO at JupiterOne, called the 17.2 million attack “significant” and told ZDNet that the ability for a DDoS attack to reach that level of bandwidth exhaustion means that there is a significant backend infrastructure of either compromised hosts or hosts that have been scaled up with the sole purpose of sending malicious traffic.
“The only other way to achieve these levels of bandwidth is to couple an enormous infrastructure with some kind of packet amplification technique. Either way, this is a meaningful attack that was not generated by a random attacker. This groups likely large, well funded, and dedicated,” Shields said.
Howard Ting, CEO at Cyberhaven, added that DDoS attacks are a growing problem and one that we should expect to see more of.
He noted that botnets, such as Mirai that launched the attack, heavily rely on compromised IoT devices and other unmanaged devices.
“As the number of these devices grows, so too does the potential army for DDoS attacks,” Ting said.
Cloudflare
Yoachimik said their autonomous edge DDoS protection system detected the 17.2 million attack and noted that their system is powered by a software-defined denial of service daemon they call dosd.
“A unique dosd instance runs in every server in each one of our data centers around the world. Each dosd instance independently analyzes traffic samples out-of-path. Analyzing traffic out-of-path allows us to scan asynchronously for DDoS attacks without causing latency and impacting performance,” Yoachimik said.
“DDoS findings are also shared between the various dosd instances within a data center, as a form of proactive threat intelligence sharing. Once an attack is detected, our systems generate a mitigation rule with a real-time signature that matches the attack patterns. The rule is propagated to the most optimal location in the tech stack.”
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Digitpol can assist with all stages of cyber related incidents.
Contact Digitpol’s hotlines or respond to us online.
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944
