A new Iranian threat actor has been discovered exploiting a now-addressed critical flaw in the Microsoft Windows MSHTML platform to target Farsi-speaking victims with a new PowerShell-based information stealer designed to harvest extensive details from infected machines.
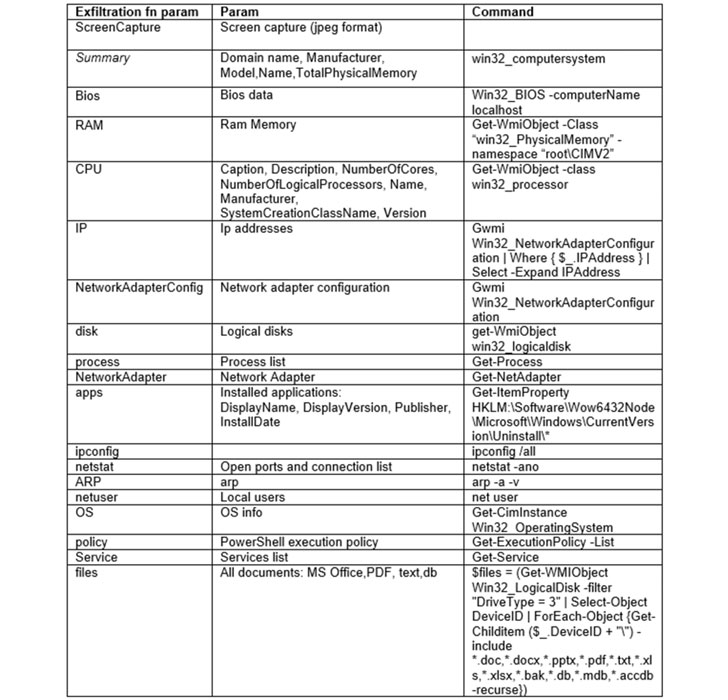
“[T]he stealer is a PowerShell script, short with powerful collection capabilities — in only ~150 lines, it provides the adversary a lot of critical information including screen captures, Telegram files, document collection, and extensive data about the victim’s environment,” SafeBreach Labs researcher Tomer Bar said in a report published Wednesday.
Nearly half of the targets are from the U.S., with the cybersecurity firm noting that the attacks are likely aimed at “Iranians who live abroad and might be seen as a threat to Iran’s Islamic regime.”
The phishing campaign, which began in July 2021, involved the exploitation of CVE-2021-40444, a remote code execution flaw that could be exploited using specially crafted Microsoft Office documents. The vulnerability was patched by Microsoft in September 2021, weeks after reports of active exploitation emerged in the wild.
“An attacker could craft a malicious ActiveX control to be used by a Microsoft Office document that hosts the browser rendering engine. The attacker would then have to convince the user to open the malicious document. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights,” the Windows maker had noted.
The attack sequence described by SafeBreach begins with the targets receiving a spear-phishing email that comes with a Word document as an attachment. Opening the file triggers the exploit for CVE-2021-40444, resulting in the execution of a PowerShell script dubbed “PowerShortShell” that’s capable of hoovering sensitive information and transmitting them to a command-and-control (C2) server.
While infections involving the deployment of the info-stealer were observed on September 15, a day after Microsoft issued patches for the flaw, the aforementioned C2 server was also employed to harvest victims’ Gmail and Instagram credentials as part of two phishing campaigns staged by the same adversary in July 2021.
The development is the latest in a string of attacks that have capitalized on the MSTHML rendering engine flaw, with Microsoft previously disclosing a targeted phishing campaign that abused the vulnerability as part of an initial access campaign to distribute custom Cobalt Strike Beacon loaders.
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Digitpol can assist with all stages of cyber related incidents.
Contact Digitpol’s hotlines or respond to us online.
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944