Business Continuity Management / Disaster Recovery
,
Cybercrime
,
Endpoint Security
Cybercrime Gangs Providing ‘No Abatement, Empathy or Free Decryptor,’ Expert Says
As the COVID-19 outbreak has intensified, so too has cybercrime, including ransomware.
With the healthcare sector being at the forefront of the global response to the disease, delivering uninterrupted care to patients is essential. But despite the claims of some criminal gangs, who pledged not to target healthcare, the sector will enjoy no magical cybercrime immunity.
“As hospitals and medical organizations around the world are working non-stop to preserve the well-being of individuals stricken with the coronavirus, they have become targets for ruthless cybercriminals who are looking to make a profit at the expense of sick patients,” says Secretary General Jürgen Stock of Interpol, the international crime-fighting agency.
While some gangs claim to no longer be targeting healthcare organizations, or to provide free decryptors for healthcare organizations, any malware infection leads to disruption, and even a free decryptor won’t replace lost time, unavailable systems and resulting delays to treatment or research (see: COVID-19 Complication: Ransomware Keeps Hitting Healthcare).
Despite some attackers’ posturing, experts say nothing has changed. “The attacks are as prevalent as ever. There has been no abatement, empathy or free decryptor granted by cybercriminals,” Bill Siegel, CEO of ransomware incident response firm Coveware, tells Information Security Media Group.
“Ransomware attacks on healthcare providers are occurring with the same frequency as this time last year. There is no ceasefire,” Brett Callow, a threat analyst at security firm Emsisoft, tells ISMG. “But it’s not only attacks on healthcare providers that are concerning; attacks on the medical supply chain could prove problematic too. In recent weeks, we’ve seen attacks on research labs, medical device manufacturers and logistics companies and all of these have the potential to indirectly impact patient care and result in the loss of life.”
In the meantime, criminals are increasingly disguising their attacks as coronavirus communications. Interpol says it is tracking attack campaigns that tap suspicious COVID-19 domains and says it is working with targeted countries to help block these attacks, many of which are trying to distribute ransomware.
“At this point, the ransomware appears to be spreading primarily via emails – often falsely claiming to contain information or advice regarding the coronavirus from a government agency, which encourages the recipient to click on an infected link or attachment,” it says.
Sodinokibi Scans for Vulnerable VPNs
While there are numerous ransomware operators at work, one of the most prolific is Sodinokibi, aka REvil and Sodin.
Sodinokibi is a ransomware-as-a-service operation that spun up in April 2019, around the time that the RaaS service GandCrab announced its retirement. Security researchers, including those at McAfee, say GandCrab appears to have at least shared its code base with Sodinokibi, although the links might run deeper.
Like its apparent progenitor, Sodinokibi affiliates sign up to receive a customized version of the ransomware from the gang that operates this scheme. Whenever an affiliate successfully infects a system and a victim pays a ransom, the affiliate receives a 60 percent to 70 percent cut of the profits (see: Sodinokibi Ransomware Gang Appears to Be Making a Killing).
Cybercrime intelligence firm Intel 471 says many – if not all – of the Sodinokibi command-and-control sites that send and receive data with individually infected bots appear to be WordPress sites. “REvil ransomware configurations [point to] more than 1,000 controllers. Interestingly, the live domains we verified all were WordPress websites, so it is probable they might be compromised by the operators or purchased from other cybercriminals,” Intel 471 says in a blog post. The sheer number of CnC servers makes them tough to disrupt, experts say.
Data Breach: 10x Genomics
Not only hospitals are under attack. On Wednesday, life sciences firm 10x Genomics, based in Pleasanton, California, reported in a Securities and Exchange Commission form 8-K filing that it had been hit by “an attempted ransomware attack” taht may have resulted in a data breach, although it said it was able to quickly recover.
“The company isolated the source of the attack and restored normal operations with no material day-to-day impact to the company or the company’s ability to access its data,” according to the filing. “The company’s investigation of the attack is ongoing with assistance from outside experts, and the company is also working with law enforcement officials on their ongoing criminal investigation of this matter.”
On March 13, the Israeli security researcher Under the Breach reported that Sodinokibi attackers claimed to have stolen 1 TB of data from 10x Genomics.
REvil/Sodinokibi #Ransomware group claiming they took 1TB worth of data from 10x Genomics (@10xGenomics), American biotechnology company that is traded on NASDAQ.
-posted samples, Will publish more files in 3 days if not paid.
-10x Genomics appear to be working on #coronavirus. pic.twitter.com/ftMxlr9lUa— Under the Breach (@underthebreach) March 13, 2020
“It is particularly disappointing that we would be attacked at a time when our products are being used widely by researchers around the world to understand and fight COVID-19,” 10x Genomics says in a statement provided to Cyberscoop.
Surge in Sodinokibi Scans
Last week, Microsoft warned that had been seeing an uptick in Sodinokibi attacks, including affiliates looking for vulnerable VPN installations (see: COVID-19 Crisis: How to Manage VPNs).
“REvil – also known as Sodinokibi – is one of the ransomware campaigns that actively exploit gateway and VPN vulnerabilities to gain a foothold in target organizations,” security researchers at Microsoft wrote in a blog post. “After successful exploitation, attackers steal credentials, elevate their privileges and move laterally across compromised networks to ensure persistence before installing ransomware or other malware payloads.”
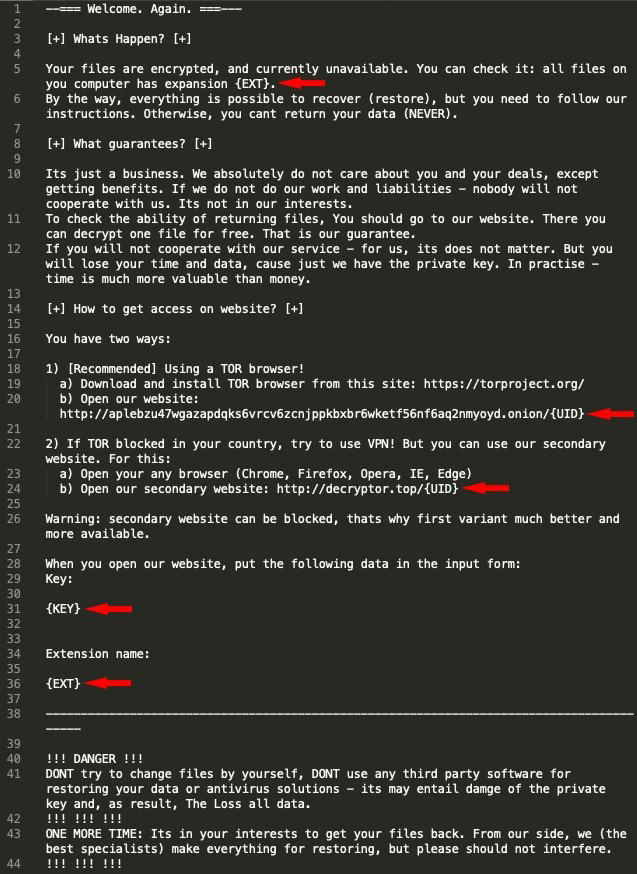
With more employees suddenly working remotely as many governments have ordered residents to stay at home whenever possible, to help blunt the spread of COVID-19, some organizations appear to be struggling to manage the increased demand (see: Is COVID-19 Driving a Surge in Unsafe Remote Connectivity?).
Weak Point: Unpatched VPN Servers
Some VPN installations are an enterprise security weak point. “As organizations have shifted to remote work in light of the pandemic, we’re seeing … that the attackers behind the REvil ransomware are actively scanning the internet for vulnerable systems,” the Microsoft researchers say. “Attackers have also been observed using the updater features of VPN clients to deploy malware payloads.”
In October 2019, the U.S. National Security Agency and U.K. National Cyber Security Center warned organizations using Pulse Secure, Fortinet and Palo Alto VPN products to ensure they had installed the latest patches (see: NSA Is Latest Intelligence Agency to Sound VPN Patch Alarm).
The NCSC warned that attackers were actively exploiting unpatched VPN servers, especially in the “government, military, academic, business and healthcare” sectors.
Many organizations have failed to install these critical patches in a timely manner. For example, ransomware victims Finastra and Travelex appear to have been hacked via unpatched VPN infrastructure – unpatched Citrix gateway servers and unpatched Pulse Secure VPN servers, respectively.
Many Fortinet servers also remain unpatched against CVE-2018-13379 – one of the flaws flagged by the NSA and NCSC, that attackers can use to easily steal plaintext passwords and usernames from servers.
Incident response expert David Stubley, who heads Edinburgh, Scotland-based security testing firm and consultancy 7 Elements, says that as of Tuesday, his internet scans have counted more than 200,000 Fortinet VPN servers globally that have HTTP-accessible login pages, of which 12,589 appear to remain unpatched to fix the flaw, down from 22,000 in October 2019 and 16,223 in January. Looking at a country level, 296 unpatched servers remain in the U.K., he says (see: Patch or Perish: VPN Servers Hit by Ransomware Attackers).
Multiple Hospitals Remain Vulnerable
Among the organizations that have failed to patch critical flaws in their VPN infrastructure are “several dozens of hospitals with vulnerable gateway and VPN appliances in their infrastructure,” says Microsoft, adding that it’s alerted them to the flaws.
“To help these hospitals, many already inundated with patients, we sent out a … targeted notification with important information about the vulnerabilities, how attackers can take advantage of them, and a strong recommendation to apply security updates that will protect them from exploits of these particular vulnerabilities and others.”
Amid the chaos of the COVID-19 pandemic, and many hospitals struggling to manage massive case loads, did these alerts help – and were they even noticed? Microsoft has not yet responded to requests for comment about how many hospitals it alerted, via what channel and how many hospitals confirmed receipt of the alerts and have now applied the patches.
Recommendation: Prevent and Mitigate
In the meantime, attacks seem set to surge. “The number of cyberattacks is significant and expected to increase further,” Europol says in a recently released report into pandemic profiteering by attackers who are exploiting the COVID-19 crisis.
“Cybercriminals will continue to innovate in the deployment of various malware and ransomware packages themed around the COVID-19 pandemic,” it says. “They may expand their activities to include other types of online attacks.”
Europol Executive Director Catherine De Bolle notes: “While many people are committed to fighting this crisis and helping victims, there are also criminals who have been quick to seize the opportunities to exploit the crisis. This is unacceptable: Such criminal activities during a public health crisis are particularly threatening and can carry real risks to human lives.”
Unfortunately, they’re not going to stand down. In the meantime, proactive patching, of course, remains among the best practices for preventing and mitigating ransomware attacks, Interpol says. “To minimize the risk of disruption in the event a ransomware attack does occur, Interpol encourages hospitals and healthcare companies to ensure all their hardware and software are regularly kept up to date. They should also implement strong safety measures like backing up all essential files and storing these separately from their main systems.”
Pro-Bono Help
To help, some security professionals and organizations – including Coveware and Emsisoft – have offered to provide free assistance to any healthcare organization that gets hit by ransomware (see: More Ransomware Gangs Join Data-Leaking Cult).
“So far, we have assisted about half a dozen victims under our pro-bono offer, including one large hospital,” says Coveware’s Siegel.
Siegel also emphasizes that healthcare is not the only sector being hit with an increasing number of ransomware attacks. “Schools are getting disproportionately hit as they have had to make radical changes to their networks to support remote work and remote learning,” he says.
[ad_2]
Article Source link
Is your business effected by a COVID-19 / Coronavirus related Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Contact Digitpol’s hotlines or respond to us online.
Digitpol is available 24/7.
Email: info@digitpol.com
Europe +31558448040
UK +44 20 8089 9944
ASIA +85239733884
