A cross-site scripting (XSS) vulnerability has been found in a WYSIWYG editor used by at least 30,000 websites.
Discovered by Bishop Fox security consultant Chris Davis and publicly disclosed on Wednesday, the bug, tracked as CVE-2021-28114, impacts Froala version 3.2.6 and earlier.
Froala is a lightweight What-You-See-Is-What-You-Get (WYSIWYG) HTML rich text editor for developers and content creators.
Wappalyzer estimates that Froala is in use by approximately 30,000 web domains.
According to Bishop Fox, the WYSIWYG editor contains a security flaw in its HTML sanitization parsing protocol, allowing attackers to bypass existing XSS protections.
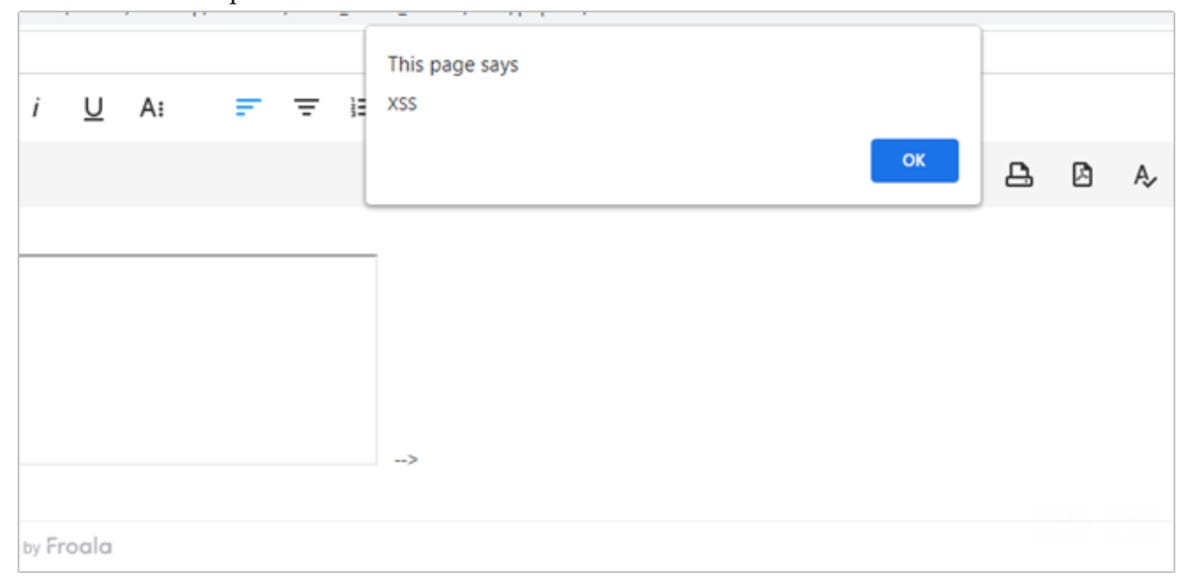
The vulnerability can be triggered by inserting a JavaScript payload in an HTML event handler within specific HTML and MathML tags, which will cause the parser to mutate the payload into JavaScript commands.
“The XSS is caused by a confusion during the HTML parsing sequence,” Davis said. “The < math > tag causes the parser to switch its namespace context from HTML to MathML, which does not parse in the same manner as HTML. The < iframe > and embedded HTML comment < !– causes the parser to switch context during the tokenization phase of HTML parsing and read the strings that follow as user data (RCDATA) rather than computer instructions.”
Bishop Fox
As a result, XSS can be triggered. Cross-site scripting attacks often allow attackers to act as a victim user when they interact with a vulnerable application, and consequences can range from privilege escalation to data leaks or, in the worst scenarios, actions such as forcing an unauthorized fund transfer.
“In Froala’s case the vulnerability may reflect itself as either stored or reflected depending on the application that uses it and therefore the impact will vary,” the researcher says. “The context of the application leveraging Froala will also dictate the impact of the vulnerability.”
CVE-2021-28114 was first discovered on February 26 and Froala was contacted on March 4. The vendor developed and released a patch in version 3.2.7 on May 18, however, Bishop Fox retested the software and found that the bug, in some configurations, had not been fully resolved. While a public disclosure timeline extension was offered, no adjustments were made.
When contacted, the vendor pointed us to the changelog. XSS bugs were previously patched in versions 3.2.2 and 3.2.3.
To mitigate the risk of this vulnerability, users should upgrade to at least version 3.2.7. The latest version available, v.4.0, was released on June 1.
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Digitpol can assist with all stages of cyber related incidents.
Contact Digitpol’s hotlines or respond to us online.
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944
