Introduction
Open Web Application Security Project (OWASP), a non-profit foundation dedicated to web application security, has recently published its latest Top 10 web application security (AppSec) risks (OWASP Top 10). Widely recognized in the IT industry, OWASP Top 10 is a standard awareness document providing ranking of, impacts, samples, and preventive measures for the most critical AppSec risks. It serves as the de facto industry AppSec standard helping organizations and developer as a starting point for secure development since its initial release in 2003. To keep pace with the changes in the AppSec market, the list is refreshed every three to four years. As an updated OWASP Top 10 has been released, HKCERT would use this opportunity to summarise the changes and analyse the 3 new categories in the new release.
What make OWASP Top 10 the benchmark standard?
The list presents the most impactful risks of AppSec in a categorised and prioritised basis for organisations to focus on prevention and mitigation. The 2021 edition of OWASP Top 10 is compiled by two methods: eight out of the ten categories come from statistical data of over 500,000 applications, while the other two are selected from a survey of front line practitioners on the highest risks. According to OWASP, this mixed approach is adopted as the statistical data only reflects known facts from the past but may not cover recent trends, an area which is complemented the survey results.
For the current edition, it has been enhanced with the analysis of close to 400 Common Weakness Enumerations (CWEs) instead of 30 previously, which ultimately change the structure of the categories which are being ranked based on the score calculation on exploitability and impact.
This make OWASP Top 10 one of the most comprehensive standards for web application security.
What is changed compared to 2017 release?
OWASP Top 10 for 2021 can be found at https://owasp.org/Top10/
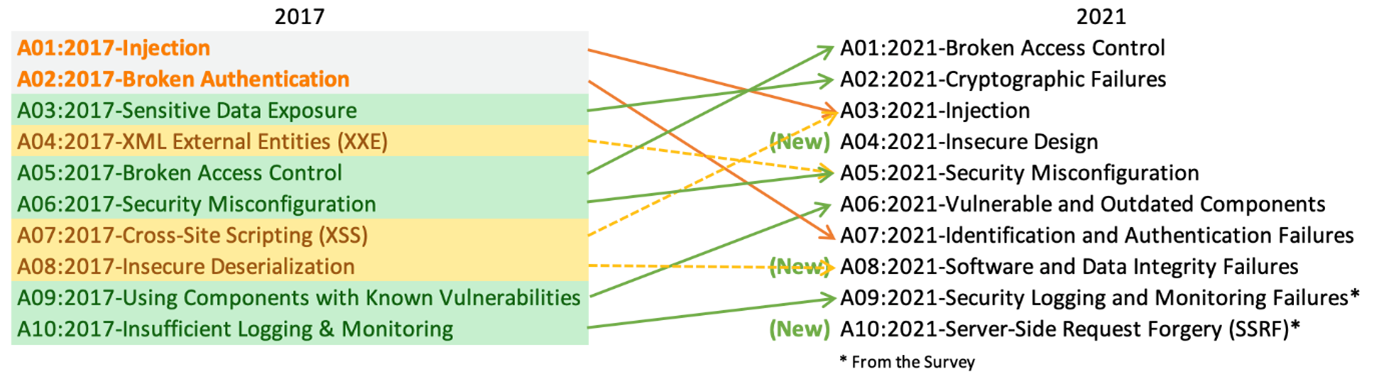
Compared with the last release in 2017, all the categories have been retained for 2021, with some being consolidated with broader scoping and ranking. Changes are summarised below:
- Sensitive Data Exposure, previously classified as broad symptom, is re-categorised as Cryptographic Failures which is the root cause that may lead to sensitive data exposure or system compromise.
- Cross-Site Scripting (XSS) now comes under the broader Injection category. Technically it is a script injection targeting other users who have accessed the affected website. It is different from other server side injection methods such as SQL, OS command, LDAP injections, which target vulnerable servers. Yet the mitigations are similar, which are input validation and contextual output encoding.
- XML External Entities (XXE) has gone into Security Misconfiguration category, since it is often a mistake made by the developer to wrongly configure the XML parsers in their code.
- Insecure Deserialization is placed under Software and Data Integrity Failures. It is a problem of insufficient protection of serialized objects, which lead to data tampering and being passed to the application from untrusted source. The unauthorised manipulation of object properties may cause application logic flaw or even lead to remote code execution (RCE) on the target system. Significant number of insecure deserializations is attributed to open source vulnerability which must be actively managed and should not be overlooked.
* Source: https://owasp.org/Top10/
There are three new categories: “A04:2021-Insecure Design”, “A08:2021-Software and Data Integrity Failures” and “A10:2021-Server-Side Request Forgery”.
A04:2021 – Insecure Design
It focuses on risks associated with the design and architectural flaws. The system logic cannot effectively prevent attacks, or there is no built-in program to handle abnormal or abuse situations, which may cause abnormal behaviours in the network application system. It may lead to unexpected behaviours of the web application. The data leakage incident at Facebook in early 2021 was one of such recent examples. The large amount of personal data was believed to be obtained by data scraping and was sold in hacker forum. It is caused by ineffective rate limit and data limit implemented by the Facebook, which permitted excessive access to data using automated tool. Use of secure development lifecycle, secure design pattern and threat modelling are recommended to address this risk.
A08:2021 – Software and Data Integrity Failures
It is one of the most impactful risks. It focuses on risks without verifying integrity during software updates, critical data, and CI/CD pipelines. Insecure Deserialization category in 2017 is now grouped under this category. It relates to code or infrastructure not protected against integrity violations. In Dec 2020, a network management software company SolarWinds was hacked and injected malicious code into the development environment. Without an effective process to verify the code integrity, the malicious code was delivered to over 18,000 organisations and caused one of the most serious cyber attacks to date. Code signing, use of trusted repositories and software supply chain security tool are preventives measures that can be deployed to neutralise such threats.
A10:2021 – Server-Side Request Forgery (SSRF)
This is the last category newly added to the current release based on the industry survey to raise our attention and awareness. It refers to web application that is able to fetch a web resource based on a user-provided URL. Depending on the purposes of the URL fetching of the affected web application, hacker exploiting the SSRF vulnerability would normally gain unauthorised access to sensitive data and may be escalated to remote code execution with additional conditions. It is also one of the major attack vectors on cloud given the cloud is built around the web which is common for cloud service providers to use HTTP endpoints to process data. In Jan 2021, the Accellion File Transfer Appliance data breach incident was caused by the SSRF vulnerability on the system (CVE-2021-27103). The hacker accessed a local SOAP web service which would not be accessible from the Internet. Developer can implement defence-in-depth controls at network layer and application layer to prevent SSRF.
Recommendation
OWASP Top 10 helps to raise awareness of the web application security threat to organisations and developers. HKCERT highly recommends companies to adopt the list as a starting point of creating a secure coding development culture. The official website contains actionable information and can serve as a checklist and internal web application development standard for the organizations.
Keep in mind that OWASP Top 10 are not the only vulnerabilities of web application since they only list the high-level category of and most significant security risks commonly found in web application. There are also many other useful resources for the security of web application. Examples include the OWASP Application Security Verification Standard, which is a list of security requirement or tests, and CWE, which breaks down each category in OWASP into details and cover other vulnerabilities that should not be neglected. Apart from taking market standards as development reference, a thorough understanding of security risks and threat modelling also hold the keys to a secure development.
“Not to be bound by typical attack patterns but try to abstract out the concept of the top 10 and apply proper judgement and reasoning in analysing application security.” OWASP HK Chapter Lead Boris So explains.
Don’t just stop at OWASP Top 10 and happy coding!
Reference:
The new Top 10 are
- A01:2021-Broken Access Control
- A02:2021-Cryptographic Failures
- A03:2021-Injection
- A04:2021-Insecure Design
- A05:2021-Security Misconfiguration
- A06:2021-Vulnerable and Outdated Components
- A07:2021-Identification and Authentication Failures
- A08:2021-Software and Data Integrity Failures
- A09:2021-Security Logging and Monitoring Failures *
- A10:2021-Server-Side Request Forgery *
* Added from industry survey
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Digitpol can assist with all stages of cyber related incidents.
Contact Digitpol’s hotlines or respond to us online.
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944


