Threat actors are exploiting improperly-secured Google Cloud Platform (GCP) instances to download cryptocurrency mining software to the compromised systems as well as abusing its infrastructure to install ransomware, stage phishing campaigns, and even generate traffic to YouTube videos for view count manipulation.
“While cloud customers continue to face a variety of threats across applications and infrastructure, many successful attacks are due to poor hygiene and a lack of basic control implementation,” Google’s Cybersecurity Action Team (CAT) outlined as part of its recent Threat Horizons report published last week.
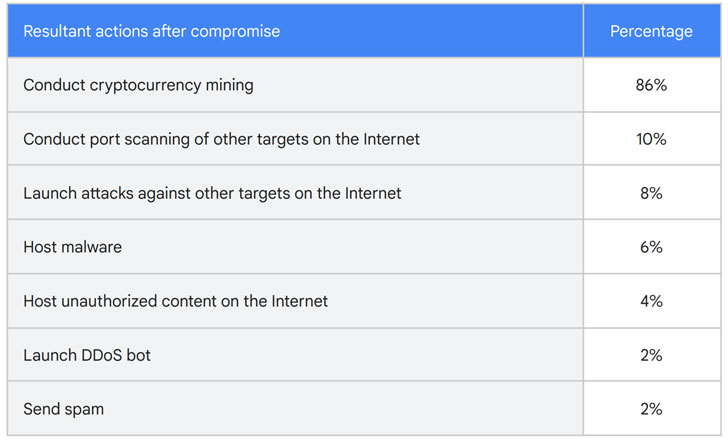
Of the 50 recently compromised GCP instances, 86% of them were used to conduct cryptocurrency mining, in some cases within 22 seconds of successful breach, while 10% of the instances were exploited to perform scans of other publicly accessible hosts on the Internet to identify vulnerable systems, and 8% of the instances were used to strike other entities. About 6% of the GCP instances were used to host malware.
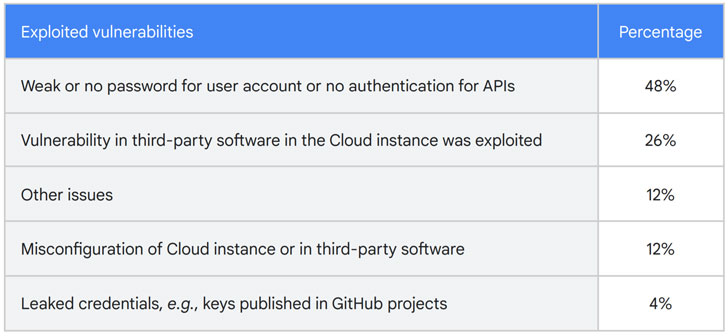
In most cases, the unauthorized access was attributed to the use of weak or no passwords for user accounts or API connections (48%), vulnerabilities in third-party software installed on the cloud instances (26%), and leakage of credentials in GitHub projects (4%).
Another attack of note was a Gmail phishing campaign launched by APT28 (aka Fancy Bear) towards the end of September 2021 that involved sending an email blast to over 12,000 account holders primarily in the U.S., U.K., India, Canada, Russia, Brazil, and the E.U. nations with the goal of stealing their credentials.
Furthermore, Google CAT said it observed adversaries abusing free Cloud credits by using trial projects and posing as fake startups to engage in traffic pumping to YouTube. In a separate incident, a North Korean government-backed attacker group masqueraded as Samsung recruiters to send fake job opportunities to employees at several South Korean information security companies that sell anti-malware solutions.
“The emails included a PDF allegedly claiming to be of a job description for a role at Samsung; however, the PDFs were malformed and did not open in a standard PDF reader,” the researchers said. “When targets replied that they could not open the job description, attackers responded with a malicious link to malware purporting to be a ‘Secure PDF Reader’ stored in Google Drive which has now been blocked.”
Google connected the attacks to the same threat actor that previously set its sights on security professionals working on vulnerability research and development earlier this year to steal exploits and stage further attacks on vulnerable targets of their choice.
“Cloud-hosted resources have the benefit of high availability and ‘anywhere, anytime’ access,” Google CAT said. “While cloud-hosted resources streamline workforce operations, bad actors can try to take advantage of the ubiquitous nature of the cloud to compromise cloud resources. Despite growing public attention to cybersecurity, spear-phishing and social engineering tactics are frequently successful.”
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Digitpol can assist with all stages of cyber related incidents.
Contact Digitpol’s hotlines or respond to us online.
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944