Emotet, the notorious email-based Windows malware behind several botnet-driven spam campaigns and ransomware attacks, was automatically wiped from infected computers en masse following a European law enforcement operation.
The development comes three months after a coordinated disruption of Emotet as part of “Operation Ladybird” to seize control of servers used to run and maintain the malware network. The orchestrated effort saw at least 700 servers associated with the botnet’s infrastructure neutered from the inside, thus preventing further exploitation.
Law enforcement authorities from the Netherlands, Germany, the U.S., U.K., France, Lithuania, Canada, and Ukraine were involved in the international action.
Previously, the Dutch police, which seized two central servers located in the country, said it had deployed a software update to counter the threat posed by Emotet effectively. “All infected computer systems will automatically retrieve the update there, after which the Emotet infection will be quarantined,” the agency noted back in January.
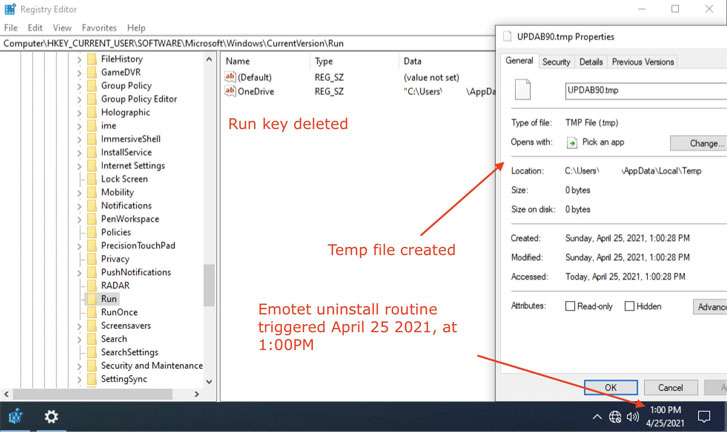
This involved pushing a 32-bit payload named “EmotetLoader.dll” via the same channels that were used to distribute the original Emotet to all compromised machines. The cleanup routine, which was set to trigger itself automatically on April 25, 2021, worked by removing the malware from the device, in addition to deleting the autorun Registry key and terminating the process.
Now on Sunday, cybersecurity firm Malwarebytes confirmed that its Emotet-infected machine that had received the specially-crafted time bomb code had successfully initiated the uninstallation routine and removed itself from the Windows system.
As of writing, Abuse.ch’s Feodo Tracker shows none of the Emotet servers are online. However, it remains to be seen if this “final” blow to the botnet will cause it to bounce back in the future or render it permanently inoperable, paving the way for other cybercrime actors to fill the void.
“Historically, Emotet’s operators used long breaks in activity to improve their malware,” Redscan researchers noted on Friday. “This means there is a realistic possibility that Emotet’s operators will use this opportunity to make the loader malware even more resilient, for example, by using polymorphic techniques to counter future coordinated action. They could also use the Emotet source code to branch off and create smaller, independent botnets.”
The mass action marks the second time law enforcement agencies have intervened to remove malware from compromised machines.
Earlier this month, the U.S. government took steps to remove web shell backdoors dropped by the Hafnium threat actor from Microsoft Exchange servers located in the country that were breached using ProxyLogon exploits.
Following the court-authorized operation, the Federal Bureau of Investigation said it’s in the process of notifying all the organizations from which it had removed web shells, implying the intelligence agency accessed the systems without their knowledge.
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Contact Digitpol’s hotlines or respond to us online.
Digitpol is available 24/7.
Email: info@digitpol.com
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944