
Vulnerabilities collectively referred to as BrakTooth are affecting Bluetooth stacks implemented on system-on-a-chip (SoC) circuits from over a dozen vendors.
The set of issues impact a wide variety of devices, from consumer electronics to industrial equipment. The associated risk ranges from denial-of-service, deadlock condition of the device to arbitrary code execution.
Wide variety of products impacted
Researchers from the Singapore University of Technology and Design have published details about BrakTooth – a new family of security vulnerabilities in commercial Bluetooth stacks.
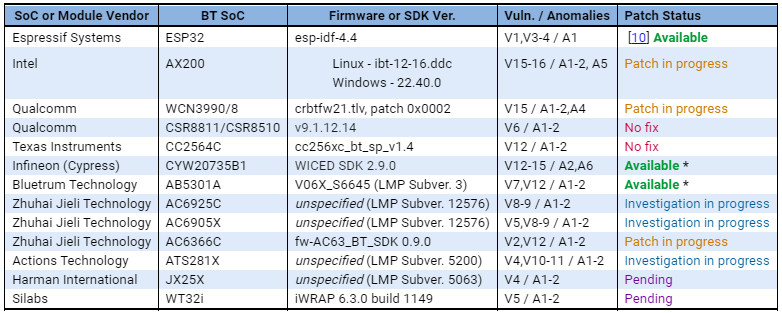
They assessed 13 Bluetooth devices from close to a dozen SoC vendors counting Intel, Qualcomm, Texas Instruments, and Cypress.
| BT SoC Vendor | BT SoC | Dev. Kit / Product | Sample Code |
| Intel (BT 5.2) | AX200 | Laptop Forge15-R | N.A |
| Qualcomm (BT 5.2) | WCN3990 | Xioami Pocophone F1 | N.A |
| Texas Instruments (BT 5.1) | CC2564C | CC256XCQFN-EM | SPPDMMultiDemo |
| Zhuhai Jieli Technology (BT 5.1) | AC6366C | AC6366C_DEMO_V1.0 | app_keyboard |
| Cypress (BT 5.0) | CYW20735B1 | CYW920735Q60EVB-01 | rfcomm_serial_port |
| Bluetrum Technology (BT 5.0) | AB5301A | AB32VG1 | Default |
| Zhuhai Jieli Technology (BT 5.0) | AC6925C | XY-WRBT Module | N.A |
| Actions Technology (BT 5.0) | ATS281X | Xiaomi MDZ-36-DB | N.A |
| Zhuhai Jieli Technology (BT 4.2) | AC6905X | BT Audio Receiver | N.A |
| Espressif Systems (BT 4.2) | ESP32 | ESP-WROVER-KIT | bt_spp_acceptor |
| Harman International (BT 4.1) | JX25X | JBL TUNE500BT | N.A |
| Qualcomm (BT 4.0) | CSR 8811 | Laird DVK-BT900-SA | vspspp.server.at |
| Silabs (BT 3.0+HS) | WT32i | DKWT32I-A | ai-6.3.0-1149 |
Digging deeper, the researchers discovered that more than 1,400 product listings are affected by BrakTooth, and the list includes but is not limited to the following types of devices:
- Smartphones
- Infotainment systems
- Laptop and desktop systems
- Audio devices (speakers, headphones)
- Home entertainment systems
- Keyboards
- Toys
- Industrial equipment (e.g. programmable logic controllers – PLCs)
Considering the variety of products affected, saying that BrakTooth affects billions of devices is likely an accurate estimation.
The researchers say that the risk associated with the BrakTooth set of security flaws ranges from denial-of-service (DoS) by crashing the device firmware, or a deadlock condition where Bluetooth communication is no longer possible, to arbitrary code.
Someone pulling a BrakTooth attack would need an ESP32 development kit, a custom Link Manager Protocol (LMP) firmware, and a computer to run the proof-of-concept (PoC) tool.
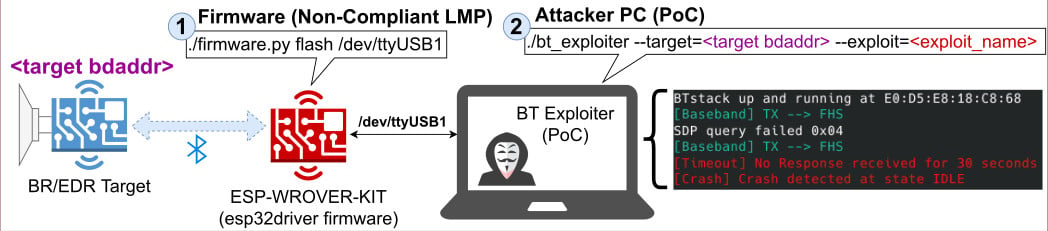
Of the 16 BrakTooth vulnerabilities, one of them tracked as CVE-2021-28139 presents a higher risk than others because it allows arbitrary code execution.
It affects devices with an ESP32 SoC circuit, which is found in numerous IoT appliances for home or industry automation.
The researchers demonstrate the attack in the video below by changing the state of an actuator using an LMP Feature Response Extended packet:
Devices running on the AX200 SoC from Intel and Qualcomm’s WCN3990 SoC are vulnerable to a DoS condition triggered when sending a malformed packet.
The list of products impacted includes laptops and desktops from Dell (Optiplex, Alienware), Microsoft Surface devices (Go 2, Pro 7, Book 3), and smartphones (e.g. Pocophone F1, Oppo Reno 5G).
The researchers informed all vendors whose products they found to be vulnerable to BrakTooh ahead of the publication of their findings but only some of them have been patched.
The vulnerabilities in the Braktooth collection target the LMP and baseband layers. Currently, they’ve been assigned 20 identifiers with a few more pending, and refer to the following 16 issues:
- Feature Pages Execution (CVE-2021-28139 – arbitrary code execution/deadlock)
- Truncated SCO Link Request (CVE-2021-34144 – deadlock)
- Duplicated IOCAP (CVE-2021-28136 – crash)
- Feature Response Flooding (CVE-2021-28135, CVE-2021-28155, CVE-2021-31717 – crash)
- LMP Auto Rate Overflow (CVE-2021-31609, CVE-2021-31612 – crash)
- LMP 2-DH1 Overflow (pending CVE – deadlock)
- LMP DM1 Overflow (CVE-2021-34150 – deadlock)
- Truncated LMP Accepted (CVE-2021-31613 – crash)
- Invalid Setup Complete (CVE-2021-31611 – deadlock)
- Host Conn. Flooding (CVE-2021-31785 – deadlock)
- Same Host Connection (CVE-2021-31786 – deadlock)
- AU Rand Flooding (CVE-2021-31610, CVE-2021-34149, CVE-2021-34146, CVE-2021-34143 – crash/deadlock)
- Invalid Max Slot Type (CVE-2021-34145 – crash)
- Max Slot Length Overflow (CVE-2021-34148 – crash)
- Invalid Timing Accuracy (CVE-2021-34147 and two more pending CVEs – crash)
- Paging Scan Deadlock (pending CVE – deadlock)
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Digitpol can assist with all stages of cyber related incidents.
Contact Digitpol’s hotlines or respond to us online.
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944


