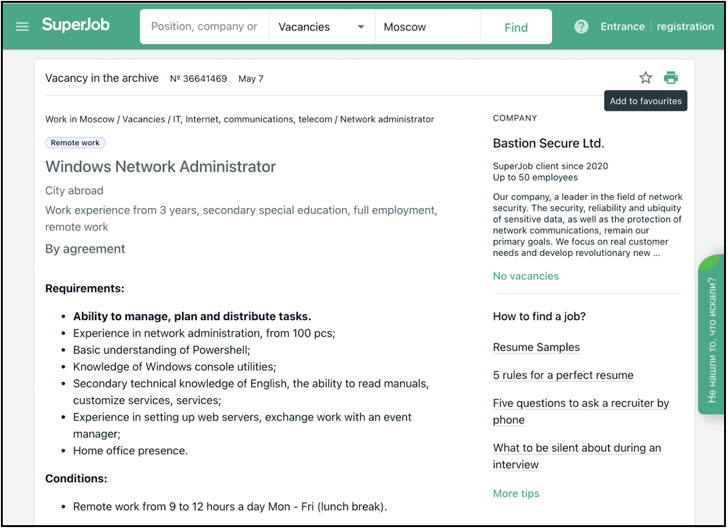
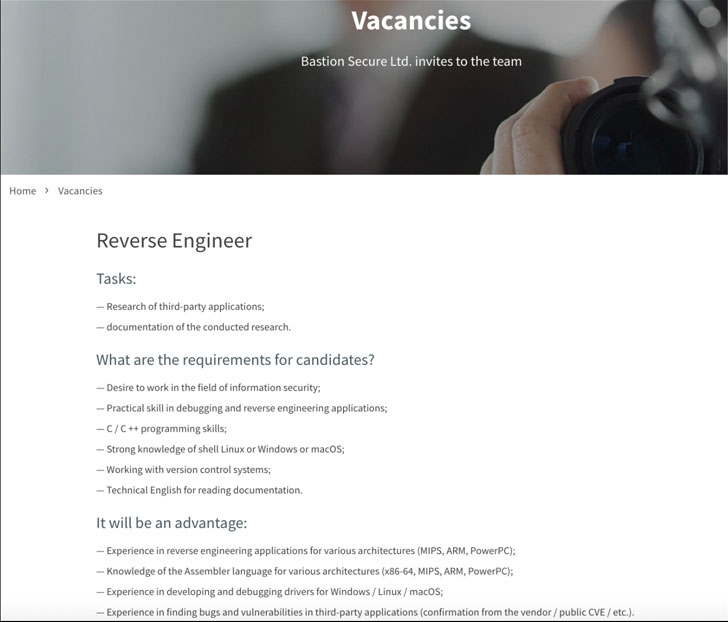
The financially motivated FIN7 cybercrime gang has masqueraded as yet another fictitious cybersecurity company called “Bastion Secure” to recruit unwitting software engineers under the guise of penetration testing in a likely lead-up to a ransomware scheme.
“With FIN7’s latest fake company, the criminal group leveraged true, publicly available information from various legitimate cybersecurity companies to create a thin veil of legitimacy around Bastion Secure,” Recorded Future’s Gemini Advisory unit said in a report. “FIN7 is adopting disinformation tactics so that if a potential hire or interested party were to fact check Bastion Secure, then a cursory search on Google would return ‘true’ information for companies with a similar name or industry to FIN7’s Bastion Secure.”
FIN7, also known as Carbanak, Carbon Spider, and Anunak, has a track record of striking restaurant, gambling, and hospitality industries in the U.S. to infect point-of-sale (POS) systems with malware designed to harvest credit and debit card numbers that are then used or sold for profit on underground marketplaces. The latest development shows the group’s expansion into the highly profitable ransomware landscape.
Setting up fake front companies is a tried-and-tested formula for FIN7, which has been previously linked to another sham cybersecurity firm dubbed Combi Security that claimed to offer penetration testing services to customers. Viewed in that light, Bastion Secure is a continuation of that tactic.
Not only does the new website feature stolen content compiled from other legitimate cybersecurity firms — primarily Convergent Network Solutions — the operators advertised seemingly genuine hiring opportunities for C++, PHP, and Python programmers, system administrators, and reverse-engineers on popular job boards, offering them several tools for practice assignments during the interview process.
These tools were analyzed and found to be components of the post-exploitation toolkits Carbanak and Lizar/Tirion, both of which have been previously attributed to the group and can be leveraged to compromise POS systems and deploy ransomware.
It’s, however, in the next stage of the hiring process that Bastion Secure’s involvement in criminal activity became evident, what with the company’s representatives providing access to a so-called client company’s network and asking prospective candidates to gather information on domain administrators, file systems, and backups, signalling a strong inclination towards conducting ransomware attacks.
“Bastion Secure’s job offers for IT specialist positions ranged between $800 and $1,200 USD a month, which is a viable starting salary for this type of position in post-Soviet states,” the researchers said. “However, this ‘salary’ would be a small fraction of a cybercriminal’s portion of the criminal profits from a successful ransomware extortion or large-scale payment card-stealing operation.”
By paying “unwitting ’employees’ far less than it would have to pay informed criminal accomplices for its ransomware schemes, […] FIN7’s fake company scheme enables the operators of FIN7 to obtain the talent that the group needs to carry out its criminal activities, while simultaneously retaining a larger share of the profits,” the researchers added.
Besides posing as a corporate entity, an additional step taken by the actor to give it a ring of authenticity is the fact that one of the company’s office addresses is the same as that of a now-defunct, U.K.-based company named Bastion Security (North) Limited. Web browsers such as Apple Safari and Google Chrome have since blocked access to the deceptive site.
“Although cybercriminals looking for unwitting accomplices on legitimate job sites is nothing new, the sheer scale and blatancy with which FIN7 operates continue to surpass the behavior shown by other cybercriminal groups,” the researchers said, adding the group is “attempting to obfuscate its true identity as a prolific cybercriminal and ransomware group by creating a fabricated web presence through a largely legitimate-appearing website, professional job postings, and company info pages on Russian-language business development sites.”
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Digitpol can assist with all stages of cyber related incidents.
Contact Digitpol’s hotlines or respond to us online.
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944