As the global community continues to pursue critical details of COVID-19, it is imperative to consider the opportunistic behavior of criminals and their intent to profit from our curiosity and concerns. In this blog, we’ll dig into mobile apps specifically.
Figure 1: CDC mobile apps ingested by SearchLight™
Our research uncovered 376 Android mobile apps related to COVID-19 as well as public health agencies like the World Health Organization (WHO) and Centers for Disease Control and Prevention (CDC).
As Google Play and Apple App stores deploy stringent verification processes to validate the legitimacy of their mobile apps, we decided to exclusively examine apps on third-party app stores. As expected, not every app was incredibly interesting or relevant: Most were benign and did not contain suspicious code. Still, there were other apps that required dangerous permissions, contained spyware, or collected sensitive user data.
Let’s dig a little deeper.
Dodgy permissions should raise eyebrows.
To set the stage, Android groups mobile app permissions into three main categories:
- Normal permissions cover areas where your app needs to access data or resources outside the app’s sandbox, but where there’s very little risk to the user’s privacy or the operation of other apps. For example, permission to set the time zone is a normal permission.
- Signature permissions are granted by the system at install time, but only when the app that attempts to use a permission is signed by the same certificate as the app that defines the permission. If the certificates match, the system automatically grants the permission without notifying the user or asking for the user’s explicit approval.
- Dangerous permissions cover areas where the app wants data or resources that involve the user’s private information or could potentially affect the user’s stored data or the operation. For example, the ability to read the user’s contacts is a dangerous permission.
Throughout our investigation, questionable permission requests came in all shapes and sizes.
We detected multiple apps that required access to perform account authentication, capture and collect photos, receive packets not directly addressed to the device, create network sockets, add and remove accounts, delete passwords, request authentication tokens, and write to the phone’s embedded SD card. While mobile app analysis tools may not detect malware within an app, requested permissions can be suspicious enough to raise concern and deter users from completing the download.
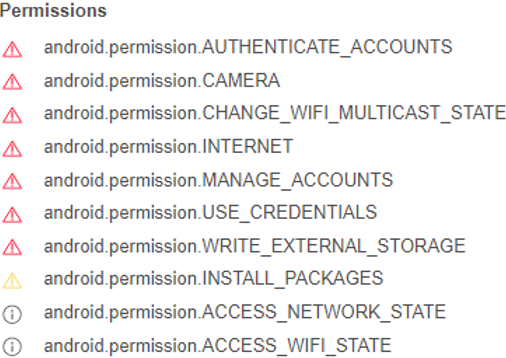
Figure 2: Permissions for coronavirus-live-statistic.apk (https://www.virustotal.com/gui/file/d0c2b6f5e8aa0eae06d6b344e394a0629f91965192a5b328e501f5bdbfacdeaa/details)
Theft-made-easy with malware.
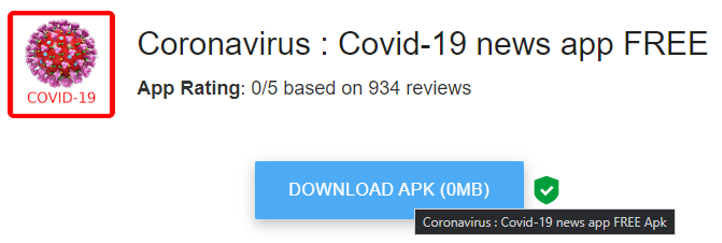
Figure 3: Screenshot of Coronavirus: Covid-19 news app FREE download link
Some mobile apps in our research didn’t even try to hide their malicious behavior.
Multiple app download links claimed to offer COVID-19-specific apps but served up an entirely different application. Some downloaded packages, specifically from AllFreeAPK, and were rigged with malicious files and required an extensive number of dangerous permissions.
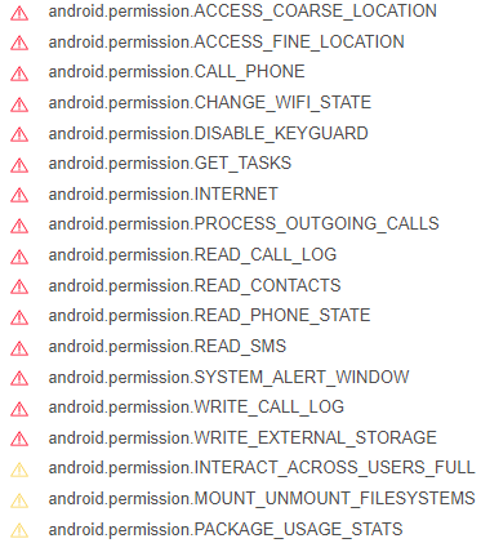
Figure 4: Permissions required for aioupdate.apk (https://www.virustotal.com/gui/file/6efba672aed4b91837758ee91b5c7bdc632cabd64df923fc702b5de24159bf19/details)
The malicious files in the downloaded apps included riskware (software whose installation and execution poses a possible yet not definite risk), adware (software that generates revenue for an attacker by automatically serving advertisements) , potentially unwanted programs (PUPs) (an application that a user may perceive as unwanted), contact collection capabilities, and SMS management capabilities.
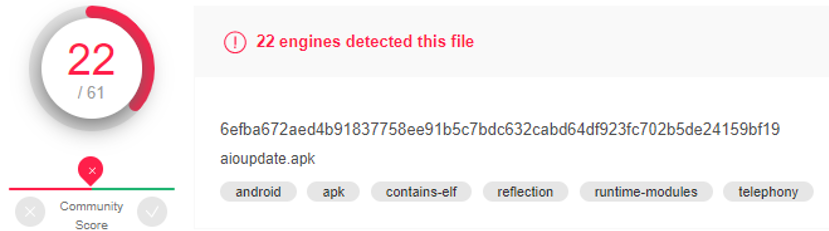
Figure 5: Malicious signatures detected in the downloaded aioupdate.apk file (https://www.virustotal.com/gui/file/6efba672aed4b91837758ee91b5c7bdc632cabd64df923fc702b5de24159bf19/detection)
Stalkerware seeks a disguise.
Researchers at mobile endpoint security company Lookout observed a malicious app, corona live 1.1, which was ostensibly part of a larger surveillance campaign targeting Libyan civilians. The app masqueraded as the legitimate Corona Live application associated with the Johns Hopkins coronavirus tracker, but requested additional access to photos, media, files, device location, and the device’s camera. The spyware within the app was identified as SpyMax, a commercialized spying tool that allows operators to manage device features and collect sensitive data.
Figure 6: Screenshot of SpyMax sample (https://blog.lookout.com/commercial-surveillanceware-operators-latest-to-take-advantage-of-covid-19)
Stalkerware (aka spyware) is one of the most invasive forms of cybercrime. Once installed on a device, stalkerware can remain undetected while managing and accessing everything on a victim’s device including sensitive information such as the target device’s camera and microphone, text messages, passwords, contact lists, stored or typed payment card details, and geo-location.
While some see stalkerware as a necessary good, it can be a serious and pervasive threat when deployed by a malicious actor. For example, governments or nation-state actors have a history of downloading spyware on journalists’ mobile devices to track their location and deter them from releasing certain information that may be considered sensitive or defamatory.
How to Mitigate Third Party Mobile App Risks
As we practice social distancing to maintain our physical health, it is also important to distance yourself from digital risk. Understanding the challenges that users face can assist in planning for potential issues that may arise. Seeking information to stay up-to-date on new data is expected during such an unfamiliar time. While nasty mobile apps provide reliable attack vectors for cybercriminals, resiliency and criticality can aid in keeping you and your device safe from adversaries’ cold grip – here’s how:
- Download apps from trusted mobile app stores. While mobile apps may be legitimate, if they’re hosted on untrusted app stores, we recommend that you avoid downloading them. Official Google Play or Apple App stores review and vet apps hosted on their platform to verify their reliability and validity; placing your trust in these platforms will usually provide a better outcome. Unfortunately, threat actors have been observed abusing official app stores’ vetting systems, so keep an eye out for out-of-place processes or suspicious activity (such as a shorter battery life) that may imply compromise.
- Remain critical of the permissions that apps request. An app that requires permission to access sensitive parts of your mobile device could possibly be used to harvest sensitive data or spread to other devices. Users often skip past the permissions that an app requests and blindly trust the download – this can lead to significant compromise. Does that new game really need access to your contact list or text messages? I don’t think so.
- Confirm that the app is created by the legitimate developer. Even if an app isn’t overtly malicious, it can still be used to mislead users. We identified multiple apps that used CDC and WHO brand imagery, but the developer name may not be verified on third-party app stores and the app certificate can be spoofed. As we have mentioned, third-party app stores cannot be trusted, but confirming the developer name before downloading from Google Play or Apple can help you recognize false information or illegitimate packages.
Want to see how we’ve helped companies detect mobile app impersonations? Check out our customer case study below.
For more threat intelligence resources on COVID-19, check out our dedicated resources page here, Coronavirus (COVID-19).
Appendix
To give more context to the type of behavior we observed, we have added a sample of apps and their associated indicators.
| Mobile app name | Indicator | App store name |
| Coronavirus Live Statistic | Dangerous permissions | Aptoide |
| Coronavírus – SUS | Dangerous permissions | Aptoide |
| Coronavirus – COVID-19 | Malware | Aptoide |
| Coronavirus : Covid-19 news app FREE | Malware | All Free APK |
| Daily News – COVID-19, Coronavirus Live Updates 1.0.4 APK | Dangerous permissions | APK Tools |
| Pandemic Tracker – CoronaVirus (COVID-19) 1.0 APK | Dangerous permissions | Full APK Download |
| COVID News – Italia APK | Malware | Download APK |
| COVID-19 Guidelines 5.10.1 APK | Dangerous permissions | APK PLZ |
[ad_2]
Article Source link
Is your business effected by a COVID-19 / Coronavirus related Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Contact Digitpol’s hotlines or respond to us online.
Digitpol is available 24/7.
Email: info@digitpol.com
Europe +31558448040
UK +44 20 8089 9944
ASIA +85239733884
