
Malware distributors are abusing a DLL hijacking vulnerability in Apple’s Push Notification service Windows executable to install coin miners on users attempting to download copyrighted software.
A common method of generating revenue on warez and crack sites, adult sites, video sharing sites, and file-sharing sites is to open low-quality web pages when a visitor attempts to view or download content.
These web pages redirect users through a series of sites that eventually push fake software updates, unwanted browser extension, fake giveaways, and malware.
A new malware campaign uses these redirects to distribute malware that uses DLL hijacking vulnerabilities to install a cryptocurrency miner on a victim’s computer.
Vulnerabilities abused Apple and CrystalBit to evade detection
A DLL hijacking vulnerability is when a legitimate program does not correctly check if the proper DLL is being loaded, and allows attackers to use their own malicious DLL instead.
One program that suffers from a known DLL hijacking vulnerability is Apple’s Push Notification service executable (APSDaemon.exe) that loads the AppleVersions.dll when executed.
As APSDaemon.exe does not check if the legitimate AppleVersions.dll is being loaded, it allows attackers to replace it with a malicious version that gets loaded instead.
This vulnerability allows the malware to run with less risk of being detected by security software as its running in a legitimate executable by Apple.
In a new campaign seen by cybersecurity firm Morphisec, attackers are using fraudulent software bundles that use DLL hijacking vulnerabilities in the Apple’s APSDaemon.exe, AnyToIso, and CrystalBit software to install coinminers.
This new malware campaign starts on sites offering cracks for copyrighted software that redirect users to a page that downloads a zip file pretending to be a setup file, key generator, or crack for a particular software.
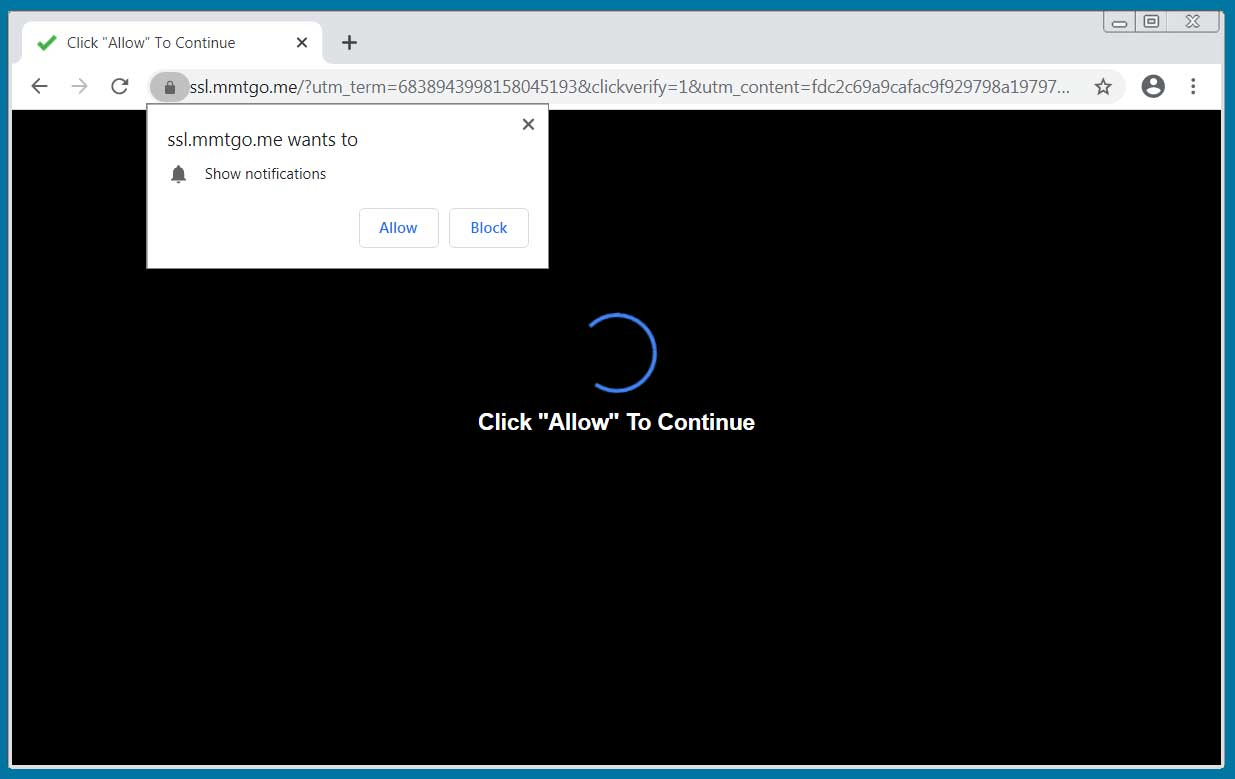
Source: BleepingComputer
According to Mophisec CTO Michael Gorelik, these files will be named in the format [random letters and digits]{7,8}_SETUP.zip, as shown below.
Source: BleepingComputer
When the executable in the ZIP archive is executed, it will install the AnyToIso or CrystalBit software and uses DLL hijacking to launch a malicious msimg32.dll file included in the zip file.
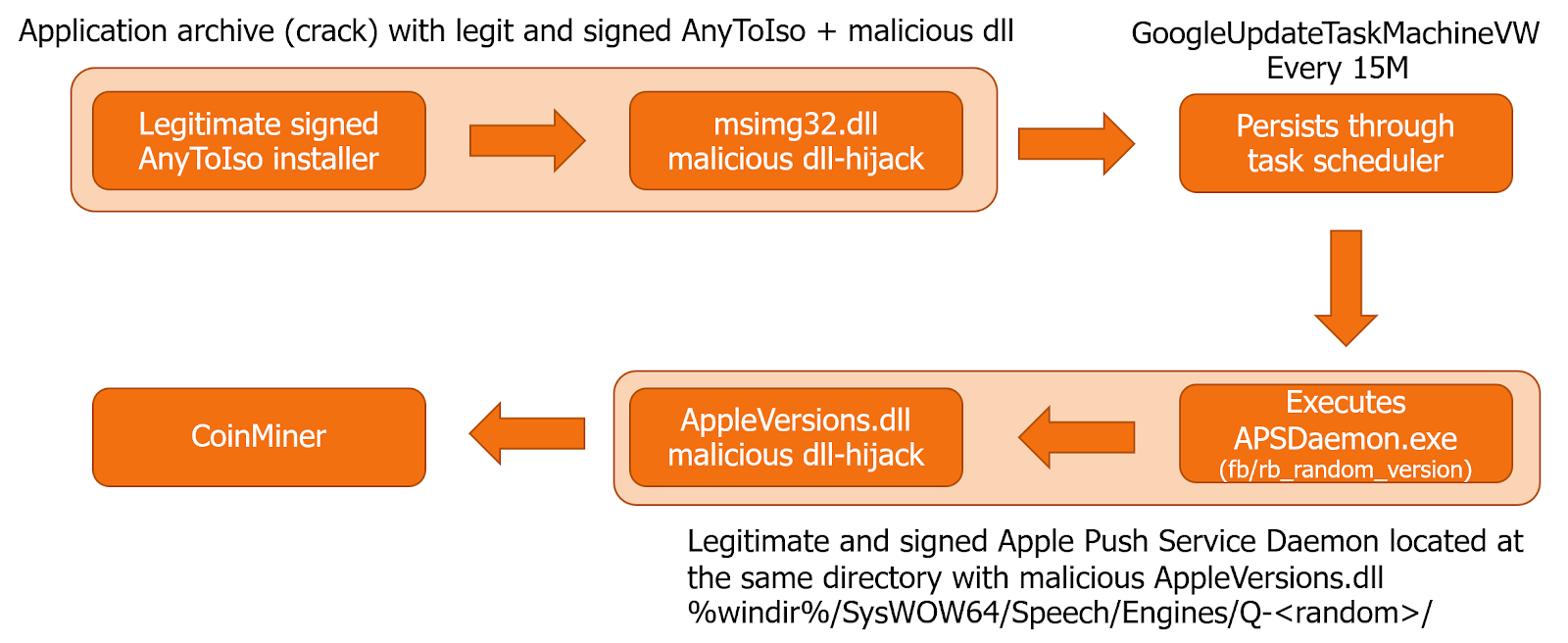
Source: Morphisec
This malicious msimg32.dll file then downloads and installs a renamed APSDaemon.exe and a malware loader renamed to Appleversions.dll into a subfolder of the C:WindowsSysWOW64SpeechEngines folder, as shown below.
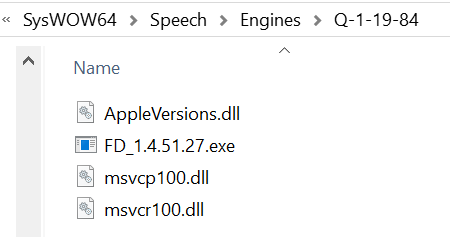
A scheduled task is then created called “GoogleUpdateTask” that launches the renamed APSDaemon.exe and the malicious AppleVersions.dll every 15 minutes with elevated privileges.
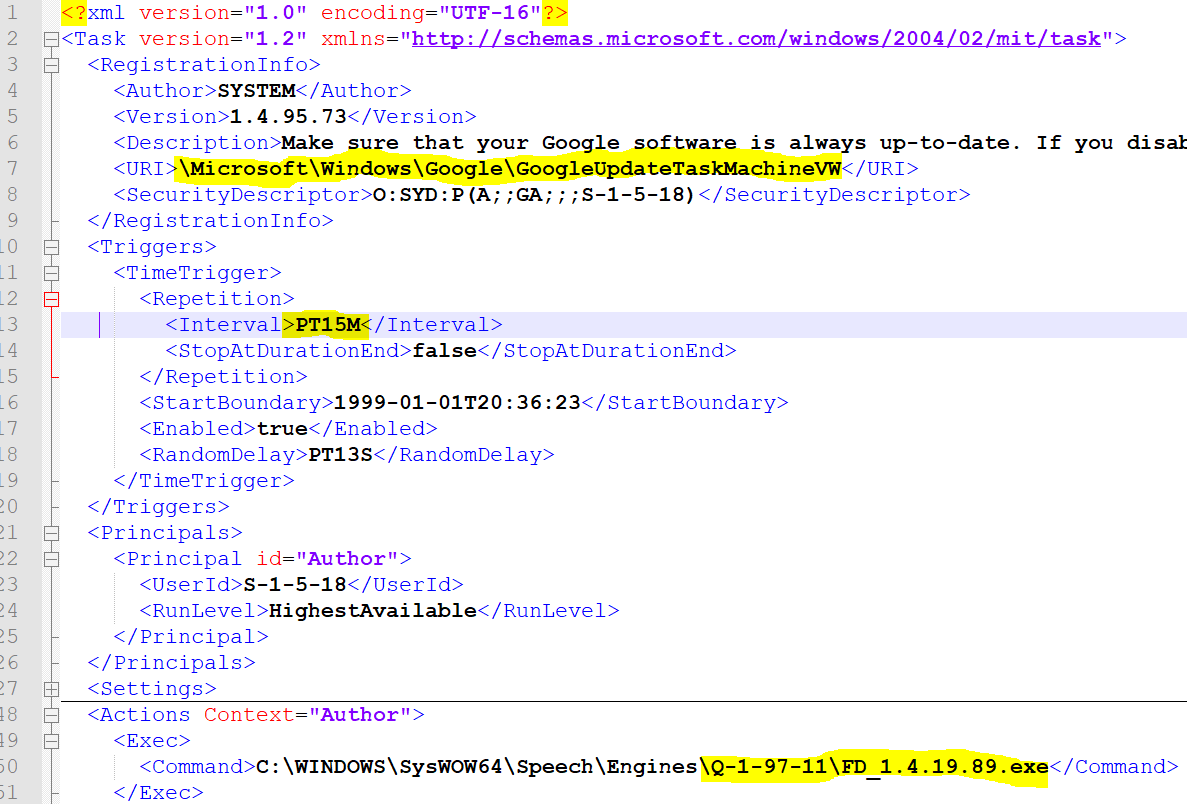
Source: Morphisec
Though the DLL hijacking in Apple’s APSDaemon.exe program may already evade detection by antivirus software, the malware developer has also used a hashing algorithm in the AppleVersions.dll to make it harder to detect as malware.
“More specifically, their shellcode implemented a variation of the Fowler–Noll–Vo hash algorithm to compare module names and function names during the iteration over the Process environment block structure. This significantly increased their chances to evade security vendors that are looking for the regular hash signatures in memory (all leading vendors are looking for the ROR-13 hash patterns as those are implemented as part of the default code injection framework unless the framework is recompiled),” Gorelik explained in his report.
With the increase in people working from home due to the COVID-19 pandemic, Gorelik warns that we will see increased distribution targeting workers in less protected environments.
“COVID-19 is the perfect time for adversaries to go hunt for new and less protected environments, WFH (work from home) is such an environment without a proper network protection stack, without proper hardening and without proper IT management and enforcement,” Gorelik warned.
Cracks and pirated software have always been a good source of malware, but now, with so many people working from home with lower protection, downloading cracks not only puts you at risk but also your company.
[ad_2]
Source link
Is your business effected by Cyber Crime?
If a cyber crime or cyber attack happens to you, you need to respond quickly. Cyber crime in its several formats such as online identity theft, financial fraud, stalking, bullying, hacking, e-mail fraud, email spoofing, invoice fraud, email scams, banking scam, CEO fraud. Cyber fraud can lead to major disruption and financial disasters. Contact Digitpol’s hotlines or respond to us online.
Digitpol is available 24/7.
Email: info@digitpol.com
ASIA +85239733884
Europe +31558448040
UK +44 20 8089 9944


